Introduction:
It’s 2021 and as the world is moving towards digitalization, we are still struggling to secure our data! The adoption of cloud services poses several concerns regarding data protection.
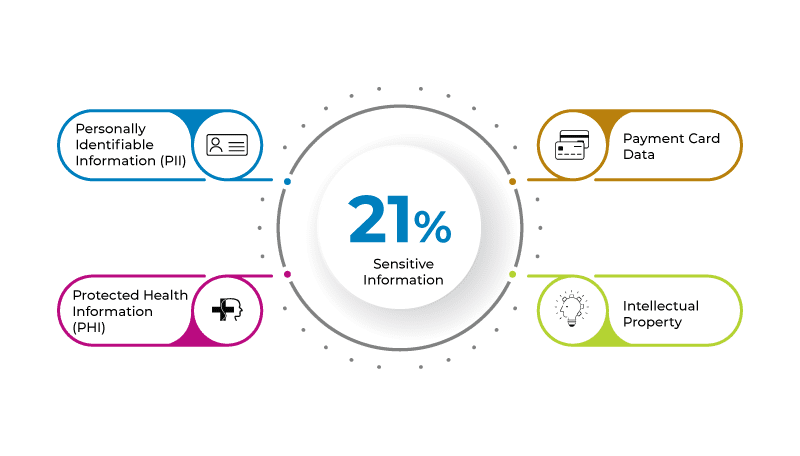
Enterprises use almost 2,000 cloud services, and employees often add new ones on their own. McAfee analyzed aggregated, anonymous files from 30 million cloud users and concluded that 21% of documents uploaded to file-sharing services contain sensitive information such as personally identifiable information (PII), protected health information (PHI), payment card data, and intellectual property, thereby raising compliance concerns.
Highlights:
According to CRN, ten of the biggest data breaches in the first half of 2021 affected more than 98.2 million people, with three of those breaches occurring in companies that deal with technology.
The average cost of a data breach for UK organizations is £2.9 million.
What explains the constant news of corporate data breaches?
- Is it the people?
The world’s top companies recruit the best. Men and women that have operational experience in the trenches, have multiple technology degrees, and are strong, pragmatic doers.
- Is it the products that are currently available?
The security technology sector has invested heavily in tools and platforms to deliver protection to our businesses and governments, regardless of whether they are backed by Wall Street behemoths or venture capital firms.
- Is it a lack of Executive support?
CXOs are actively looking into ways to strengthen their businesses at a time when the world is turning towards digitalization and remote working is becoming the norm.
The Real Gap:
Security, Compliance, Governance teams will continue to experience catastrophic failures because the data they are attempting to protect has been delivered to them as a ‘vanilla’ container. As a vanilla container, security, compliance, and governance are asked to protect everything, from PII data and medical records to personal home finance records and the local pizza restaurant’s takeaway menu!
Fill the gap with Content-Aware Protection:
Keeping your data secure starts with data awareness.
In today’s dynamic threat landscape, traditional data leak prevention is not enough. While considering effective data security, it is important to be able to determine what information is contained in a specific file, folder, application, or other data stores, whether that information is at rest, in use, or in transit.
Data Dynamic’s Unified Unstructured Data Management Platform helps a complete analytics-driven report identifying all unstructured data by the owner, location, encryption, application creator, and Content Risk (PII data – credit cards, SS#’s, email addresses, etc.). By adopting our distinguish data management platform, Security, Compliance, and Governance teams would increase their outcomes by a factor of 100X+ with the help of the needed insights to correctly quarantine the highest risk data.
Visit – www.datadynamicsinc.com. Contact us solutions@datdyn.com or click here to to request a demo.
Reference:
- https://www.endpointprotector.com/solutions/content-aware-data-loss-prevention
- https://www.darkreading.com/risk/data-awareness-is-key-to-data-security
- https://www.cyberradarsystems.com/content-aware-data-loss-prevention
- https://www.techopedia.com/definition/31011/content-aware-data-loss-prevention-content-aware-dlp
- https://www.cyberradarsystems.com/content-aware-data-loss-prevention
- https://www.techopedia.com/definition/31011/content-aware-data-loss-prevention-content-aware-dlp
- https://www.crn.com/slide-shows/security/the-10-biggest-data-breaches-of-2021-so-far-






