What is Cybersecurity?
Cybersecurity refers to the practice of protecting systems, networks, devices, and data from unauthorized access, cyberattacks, and digital threats. It encompasses a broad set of technologies, processes, and policies designed to ensure the confidentiality, integrity, and availability of information across the digital ecosystem.
In simple terms: cybersecurity is what stands between your most valuable digital assets and the growing sophistication of cyber adversaries.
Why Cybersecurity Matters
In today’s hyperconnected world, cybersecurity is no longer a back-office IT function—it’s a business-critical capability. As enterprises accelerate cloud adoption, remote work, AI deployment, and data sharing, their attack surfaces have expanded dramatically.
From ransomware attacks and data breaches to supply chain compromises and insider threats, cyber risks are now existential risks. According to IBM’s 2024 Cost of a Data Breach Report, the global average cost of a data breach has reached $4.88 million, with detection and response taking an average of 277 days.
Modern cybersecurity isn’t about building a fortress—it’s about building resilience: anticipating threats, adapting in real time, and enabling secure digital transformation.
Key Pillars of Cybersecurity
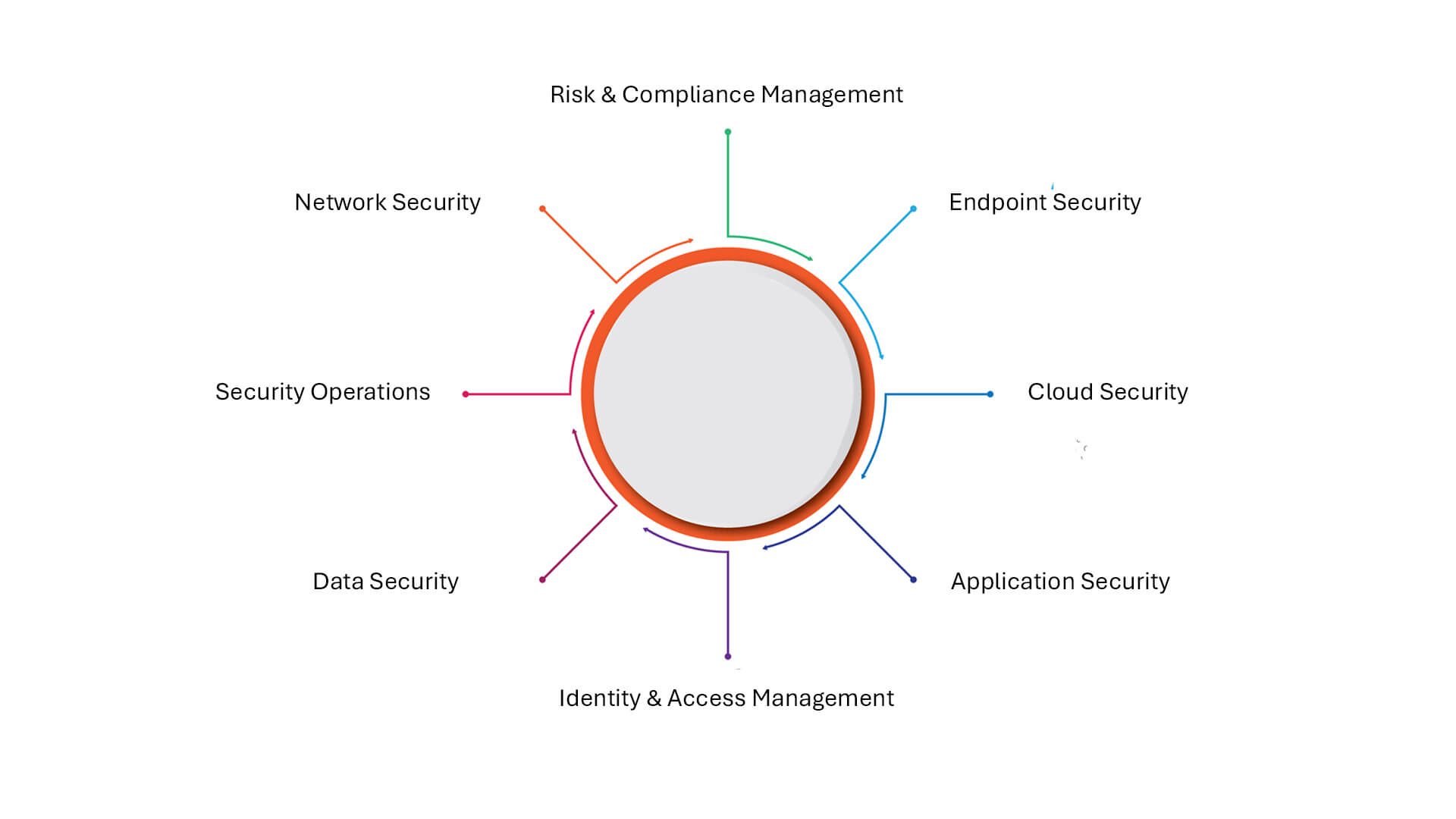
- Network Security: Protects data in transit across internal and external networks.
- Endpoint Security: Safeguards devices like laptops, servers, and mobile phones from compromise.
- Cloud Security: Ensures secure access and data protection in multi-cloud and hybrid cloud environments.
- Application Security: Identifies and mitigates vulnerabilities in software and APIs.
- Identity & Access Management (IAM): Verifies users and controls what they can access through authentication and authorization.
- Data Security: Encrypts, classifies, and governs data across its lifecycle—whether in use, in motion, or at rest.
- Security Operations (SecOps): Combines tools and teams for threat detection, incident response, and continuous monitoring.
- Risk & Compliance Management: Aligns security controls with regulatory frameworks such as GDPR, HIPAA, and DPDP.
Powering Modern Business Outcomes
- Zero Trust Architecture: Replaces perimeter-based security with identity- and context-based access control.
- Ransomware Defense: Combines endpoint detection, backups, and behavioral analytics to detect and neutralize attacks.
- Data Privacy Compliance: Enforces policies to protect personal data and prove audit readiness.
- Secure AI Pipelines: Ensures that AI models and training data are protected from tampering, leakage, or misuse.
- Insider Threat Management: Monitors anomalous behavior to prevent data theft or sabotage from within the organization.
- Cyber Resilience Planning: Integrates security with business continuity and disaster recovery strategies.
Challenges in Cybersecurity – and What to Do About Them
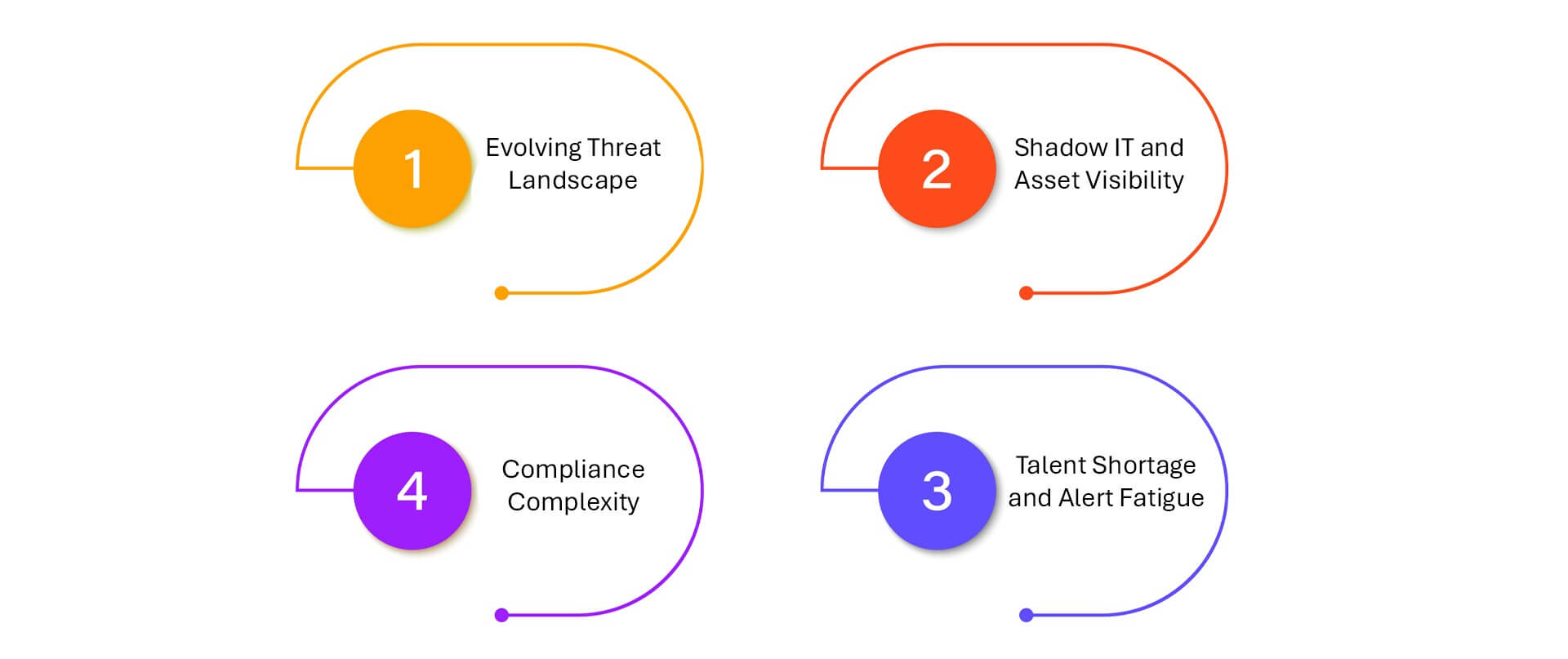
Evolving Threat Landscape
From nation-state actors to AI-generated malware, cyber threats are becoming more advanced, persistent, and unpredictable.
What to do: Invest in threat intelligence, behavior-based detection, and adversarial simulation to stay ahead of emerging tactics. Prioritize detection speed and response agility.
Shadow IT and Asset Visibility
Organizations often lose track of all the endpoints, users, and cloud instances connected to their environments.
What to do: Deploy asset discovery tools and maintain a real-time inventory of all devices, users, and workloads. Integrate visibility with access control and patch management systems.
Talent Shortage and Alert Fatigue
Security teams are overwhelmed by alerts and understaffed to handle them effectively.
What to do: Use automation and AI to prioritize threats, reduce noise, and streamline incident response. Adopt Managed Detection and Response (MDR) services where needed.
Compliance Complexity
Navigating global regulations and proving continuous compliance is resource-intensive and high-stakes.
What to do: Implement a unified security and compliance platform with real-time dashboards, audit trails, and automated policy enforcement. Align security posture with risk appetite and business goals.
Beyond the Firewall: Why Cybersecurity Is Now the Backbone of AI, Sovereignty, and Digital Trust
Cybersecurity has outgrown its roots as a defensive perimeter. In a world driven by AI, governed by data sovereignty, and defined by digital interactions, it has become the invisible infrastructure powering everything, from operational resilience to ethical governance.
As AI systems increasingly process sensitive personal, behavioral, and biometric data, cybersecurity must evolve to do more than block attacks—it must anticipate misuse, detect drift, and ensure explainability. Protecting algorithms now means protecting the data that feeds them, the models they generate, and the decisions they influence.
Meanwhile, data sovereignty has reshaped the cybersecurity mandate. Enterprises operating across borders must guarantee not just encryption, but jurisdiction-aware data governance, ensuring that information is processed, stored, and secured within the legal boundaries of each region. Cybersecurity becomes the enforcement layer for these geopolitical guardrails.
But above all, cybersecurity is now the litmus test for digital trust. Stakeholders no longer ask if you’re secure—they ask how well, how visibly, and how continuously. Security isn’t just a technical control—it’s a brand signal, a boardroom priority, and a market differentiator.
In this new reality, cybersecurity is not an endpoint. It’s an ongoing commitment to integrity, transparency, and responsible innovation. The organizations that embed it into every layer of architecture—not just tools, but culture—will lead not only in defense, but in credibility and competitive edge.
Cybersecurity is not a checkbox—it’s a strategic differentiator. It empowers innovation, unlocks trust, and ensures that the digital future is not just fast and connected, but also secure and resilient.
In a world where data is the target and disruption is constant, your ability to protect, adapt, and respond defines your ability to lead.
Getting Started with Data Dynamics:
- Learn about Unstructured Data Management
- Schedule a demo with our team
- Read the latest blog: How Data Sovereignty Is Challenging Data Governance — And What the Future Demands






