What Is LDAP?
Lightweight Directory Access Protocol (LDAP) is a time-tested standard for querying and managing directory information—most notably, user identities, access privileges, and network resources. Built for structured, hierarchical data, LDAP has long served as the backbone for enterprise authentication and authorization, providing a consistent, centralized view of identity and access across sprawling IT ecosystems.
It operates on a client-server model, allowing systems to validate user credentials, fetch user profiles, and enforce group-based permissions. In essence, it’s the protocol that answers, “Who are you, and what are you allowed to do?”—a question that’s never been more relevant than in today’s hyper-connected digital economy.
The Strategic Importance of LDAP in a Fractured Identity Landscape
In 2025, digital identity is both a frontline defense and a critical vulnerability. From ransomware attacks in critical infrastructure to state-backed cyber intrusions into government and healthcare systems, weak or mismanaged identities are often the initial entry point. As a result, identity has become the new perimeter—and protocols like LDAP remain foundational to securing it.
Even as organizations invest in modern solutions such as SSO, biometrics, and decentralized identity, LDAP continues to underpin identity verification across thousands of legacy and modern applications. It quietly powers email logins, VPN authentications, HR databases, and secure access to sensitive datasets—many of which are now subject to national and cross-border data sovereignty rules.
LDAP in the Age of AI, Zero Trust, and Global Regulation
The rise of AI and autonomous systems has expanded the attack surface and data exposure risks, making granular, auditable identity management non-negotiable. For instance, AI models trained on sensitive customer or employee data need to be governed by strict access policies. LDAP helps enforce those policies, ensuring only authorized systems and individuals can access data pipelines or inference layers.
Simultaneously, the global shift toward Zero Trust Architectures (ZTA)—championed by the U.S. federal government and emulated in private sectors worldwide—has thrust identity protocols into the spotlight. LDAP integrates with Zero Trust models by serving as the core source of identity verification, supporting real-time access decisions and adaptive policy enforcement.
Additionally, with laws like the EU’s GDPR, India’s DPDP Act, and the Middle East’s growing data sovereignty mandates, organizations must now prove who accessed what data, when, and why. LDAP logs, when properly maintained, are an essential part of the audit trail in this compliance-first world.
LDAP Is Evolving—But It’s Not Going Away
Despite the perception that LDAP is legacy tech, it’s actively evolving. Cloud-native directory services like Microsoft Azure AD DS and AWS Directory Service now offer LDAP compatibility, helping organizations bridge the gap between traditional on-prem systems and modern cloud platforms.
Moreover, as decentralized identity systems gain ground—especially in financial services and Web3 projects—LDAP is increasingly part of hybrid identity strategies. Federated identity management often uses LDAP as the authoritative store of record, integrating it with OAuth, SAML, and OpenID Connect to orchestrate seamless, secure access across multi-cloud environments.
Emerging Challenges in LDAP-Centric Environments
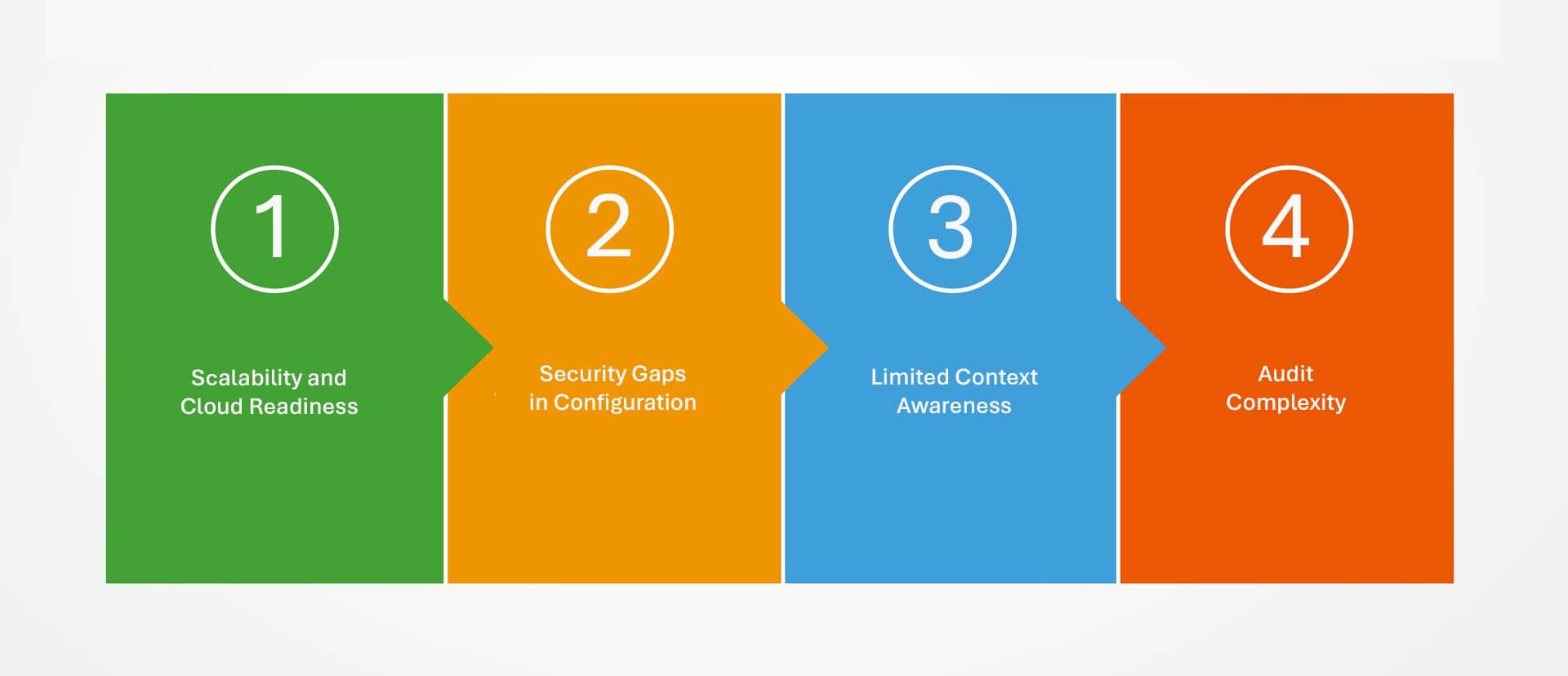
LDAP’s resilience doesn’t mean it’s without obstacles. In today’s dynamic security environment, several challenges are surfacing:
- Scalability and Cloud Readiness: Traditional LDAP deployments weren’t designed for the scale and elasticity of cloud-native systems or distributed workforces.
- Security Gaps in Configuration: Misconfigured LDAP directories remain a frequent root cause in data breaches, especially when exposed to the internet or loosely integrated with modern systems.
- Limited Context Awareness: Unlike adaptive access protocols, LDAP alone doesn’t natively support fine-grained, risk-based decisioning (e.g., block access if the user logs in from an unusual location).
- Audit Complexity: While LDAP supports basic logging, compliance today demands rich metadata—including intent, geo-location, and behavioral insights—often requiring additional tooling layered on top.
Strategic Pathways: From Foundation to Federation
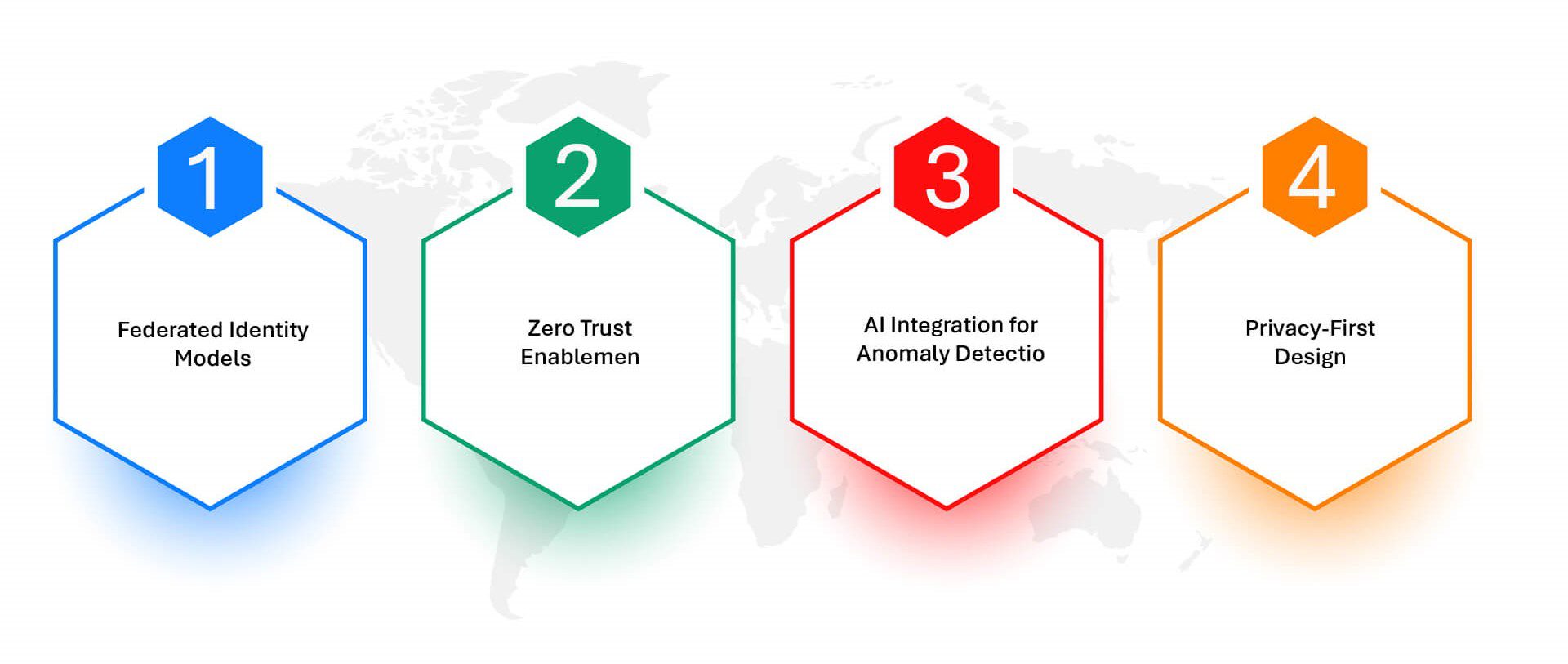
To remain relevant and secure, LDAP must evolve from a background utility to an integrated part of the enterprise’s digital trust fabric:
- Federated Identity Models: Integrating LDAP with modern IAM tools (e.g., Okta, Ping, ForgeRock) enables policy unification across hybrid environments.
- Zero Trust Enablement: LDAP should feed into real-time policy engines, combining static credentials with contextual signals like device health or network risk.
- AI Integration for Anomaly Detection: Applying ML to LDAP logs can surface unusual access patterns, helping prevent lateral movement or insider threats.
- Privacy-First Design: Given new regulatory mandates, LDAP implementations must support granular consent tracking, data minimization, and encryption at rest and in transit.
Looking Forward: LDAP as a Pillar of Digital Accountability
LDAP may not grab headlines like blockchain or quantum computing, but its strategic relevance is only growing. In a world where digital trust is currency, and where every access event could be a potential liability, LDAP offers something few protocols do: stability, transparency, and a clear lineage of digital identity.
As enterprises navigate the tension between innovation and regulation, LDAP stands as a quiet but critical enabler—anchoring AI governance, reinforcing data sovereignty, and ensuring that the right people (and machines) have access to the right data, for the right reasons.
It’s not about whether LDAP is modern enough—it’s about how enterprises modernize around it, leveraging its strengths while embedding it into a broader architecture of resilience, ethics, and trust.
Getting Started with Data Dynamics:
- Learn about Unstructured Data Management
- Schedule a demo with our team
- Read the latest Blog: The Sovereign AI Paradox: Building Autonomy Without Breaking the Business






