What is Personally Identifiable Information (PII)?
Personally Identifiable Information (PII) refers to any data that can be used to identify an individual, either on its own or when combined with other data. This includes direct identifiers such as full names, Social Security numbers, and biometric records, as well as indirect identifiers like IP addresses, birth dates, and geolocation data when used in conjunction.
PII is central to privacy regulations and data protection frameworks around the world. From customer records and employee files to behavioral analytics and online tracking, PII underpins how organizations interact with and protect individual data.
Why PII Protection Matters
In an era defined by data breaches, cyber threats, and growing regulatory scrutiny, protecting PII is more than a compliance requirement—it’s a trust mandate. A single exposed identifier can lead to identity theft, reputational damage, legal penalties, and erosion of customer confidence.
According to IBM’s Cost of a Data Breach Report 2023, breaches involving PII are the most expensive, costing organizations an average of $180 per lost or stolen record. With global privacy laws like GDPR, CCPA, and India’s DPDP Act setting stricter rules around data handling and consent, organizations must know exactly where PII resides, who has access to it, and how it’s being used.
Types of PII
- Direct PII: Data that uniquely identifies an individual (e.g., passport number, email address, biometric data).
- Indirect PII: Data that may identify an individual when combined with other information (e.g., gender, zip code, job title).
Challenges in Managing PII
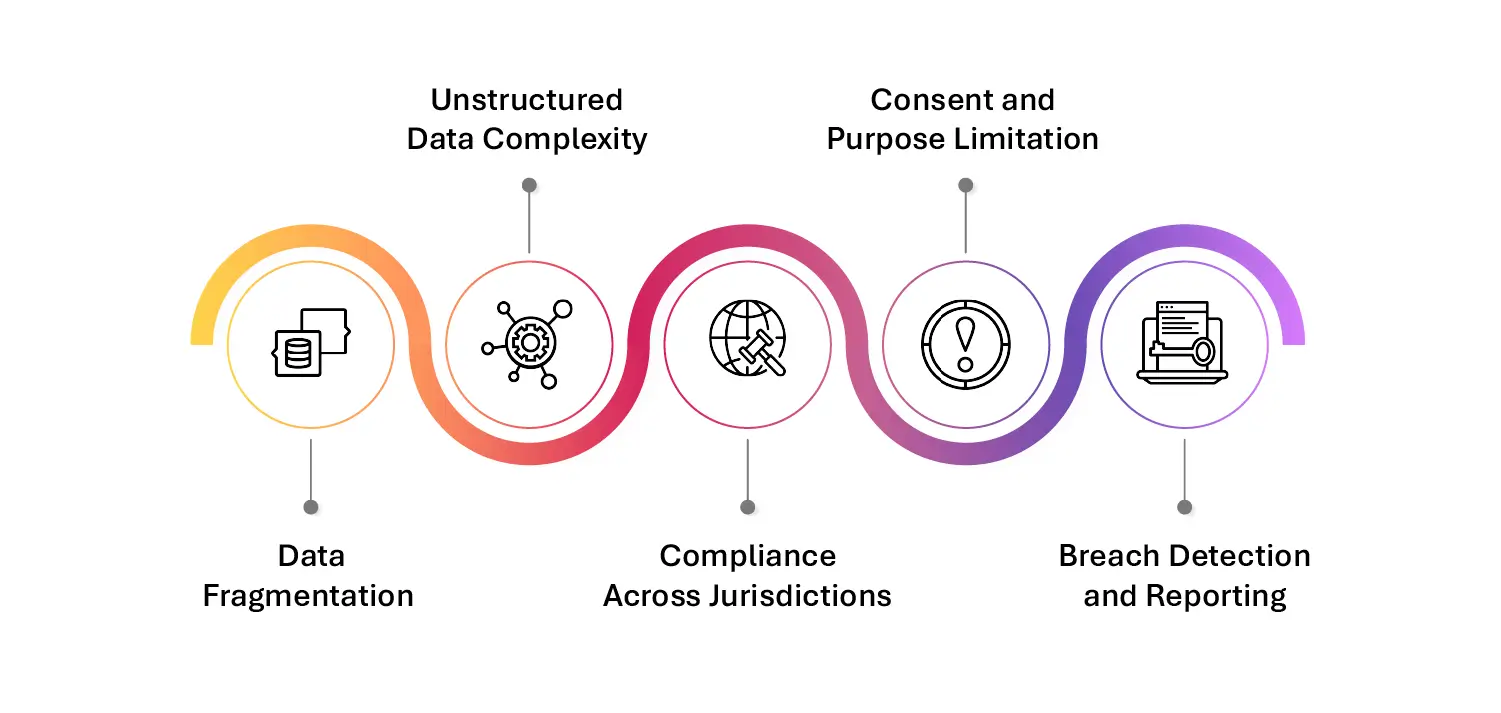
- Data Fragmentation: PII is often scattered across emails, databases, spreadsheets, and third-party platforms, making it difficult to discover and govern comprehensively.
- Unstructured Data Complexity: A large volume of PII is embedded in unstructured formats like PDFs, contracts, and scanned forms, complicating detection and classification.
- Compliance Across Jurisdictions: Organizations operating across regions must navigate a maze of global data privacy laws, each with unique definitions, requirements, and penalties around PII.
- Consent and Purpose Limitation: Tracking the purpose for which PII was collected—and ensuring it’s only used within that scope—is challenging without strong metadata and policy frameworks.
- Breach Detection and Reporting: Identifying when PII is compromised and responding within mandated timeframes (e.g., 72 hours under GDPR) demands real-time monitoring and response capabilities.
The Way Forward: Turning PII from a Risk to a Strategic Asset
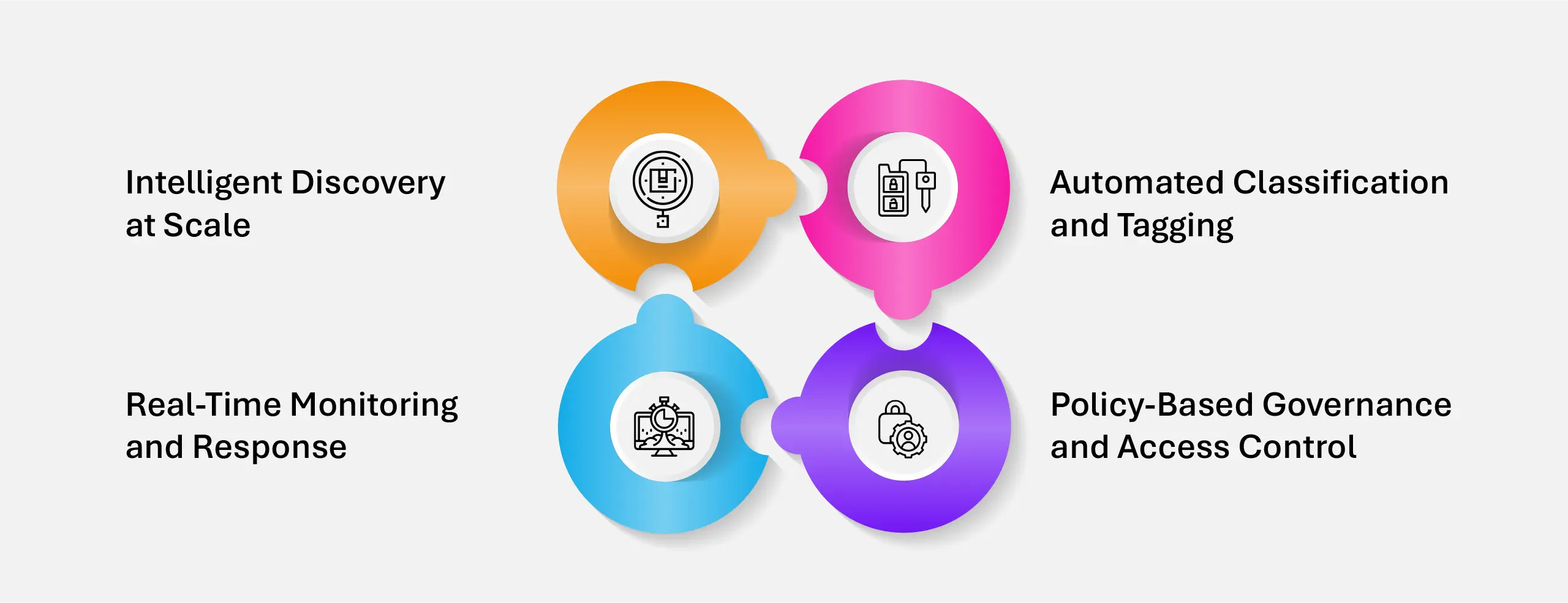
Addressing the challenges of PII isn’t just about securing data—it’s about rethinking how it’s discovered, governed, and operationalized. In a modern digital architecture, forward-thinking enterprises are adopting an integrated approach to PII management that spans visibility, context, and control.
- Intelligent Discovery at Scale: Enterprises are moving beyond manual audits and static inventories. AI-powered discovery tools now scan vast amounts of structured and unstructured data to locate PII—whether buried in legacy systems, cloud repositories, or document archives.
- Automated Classification and Tagging: To enforce policies effectively, PII must be classified by type, sensitivity, and regulatory relevance. Automation enables real-time tagging and risk scoring, ensuring high-risk data gets prioritized and handled accordingly.
- Policy-Based Governance and Access Control: Role-based access, retention schedules, encryption, and redaction are becoming non-negotiable. Centralized policy engines now ensure consistent enforcement across hybrid environments while enabling granular controls.
- Real-Time Monitoring and Response: With breach response timelines shrinking, continuous monitoring is key. Integrated systems detect anomalous access to PII, trigger alerts, and streamline forensic investigations—turning reaction into real-time mitigation.
Why PII Governance is Central to Digital Trust
In today’s data-driven economy, where digital identities are currency and privacy expectations are rising, PII governance has become a cornerstone of enterprise integrity. It’s not just about compliance—it’s about credibility. Customers, regulators, and partners want assurance that personal data is handled with care, accountability, and foresight.
Leading organizations recognize that privacy isn’t a constraint—it’s a competitive edge. Effective PII governance empowers them to build personalization with guardrails, automate compliance at scale, and confidently respond to audits or data subject rights. It transforms privacy from a legal obligation into a brand promise.
As AI systems increasingly rely on personal data and global regulations grow more nuanced, PII governance is evolving into the anchor of ethical data practices. It ensures transparency in algorithmic use, enforces data minimization, and strengthens digital trust across every interaction.
PII is no longer just a category of data—it’s the pulse of responsible innovation. Managing it intelligently shapes how enterprises navigate risk, inspire trust, and lead in an era defined by digital accountability.
Because in a world where identity is everything, how you govern PII defines who you are.
Getting Started with Data Dynamics:
- Learn about Unstructured Data Management
- Schedule a demo with our team
- Read the latest blog: Data Sovereignty Is No Longer a Policy Debate. It’s the New Rulebook for Digital Governance






