Role-Based Access Control (RBAC) is a security, governance, and compliance model that restricts system or data access based on predefined roles within an organization. Instead of assigning permissions directly to each user, RBAC enables administrators to create role profiles—each encapsulating a set of access rights—and assign them to users based on their job functions, responsibilities, or business context.
RBAC is foundational to modern identity and access management (IAM), especially in environments handling sensitive data, such as finance, healthcare, government, and AI development pipelines.
Why Organizations Can’t Ignore It
In a world where data breaches average $4.88 million per incident (IBM, 2024) and regulatory frameworks like DPDP, GDPR, HIPAA, and PCI-DSS impose strict control over who can access what data, RBAC serves as the first—and often last—line of defense.
As enterprises scale, managing individual permissions becomes untenable. Without RBAC, businesses face:
- Permission sprawl – where users accumulate access over time without proper offboarding.
- Shadow access – unauthorized or forgotten access paths to sensitive data.
- Audit complexity – difficulties in demonstrating compliance to regulators and auditors.
- AI risk exposure – where unchecked access can compromise training datasets or violate data usage policies.
RBAC provides the structural scaffolding to mitigate these challenges by enforcing least privilege, improving data visibility, and ensuring operational agility through centralized control.
Foundations of Intelligent Access Management
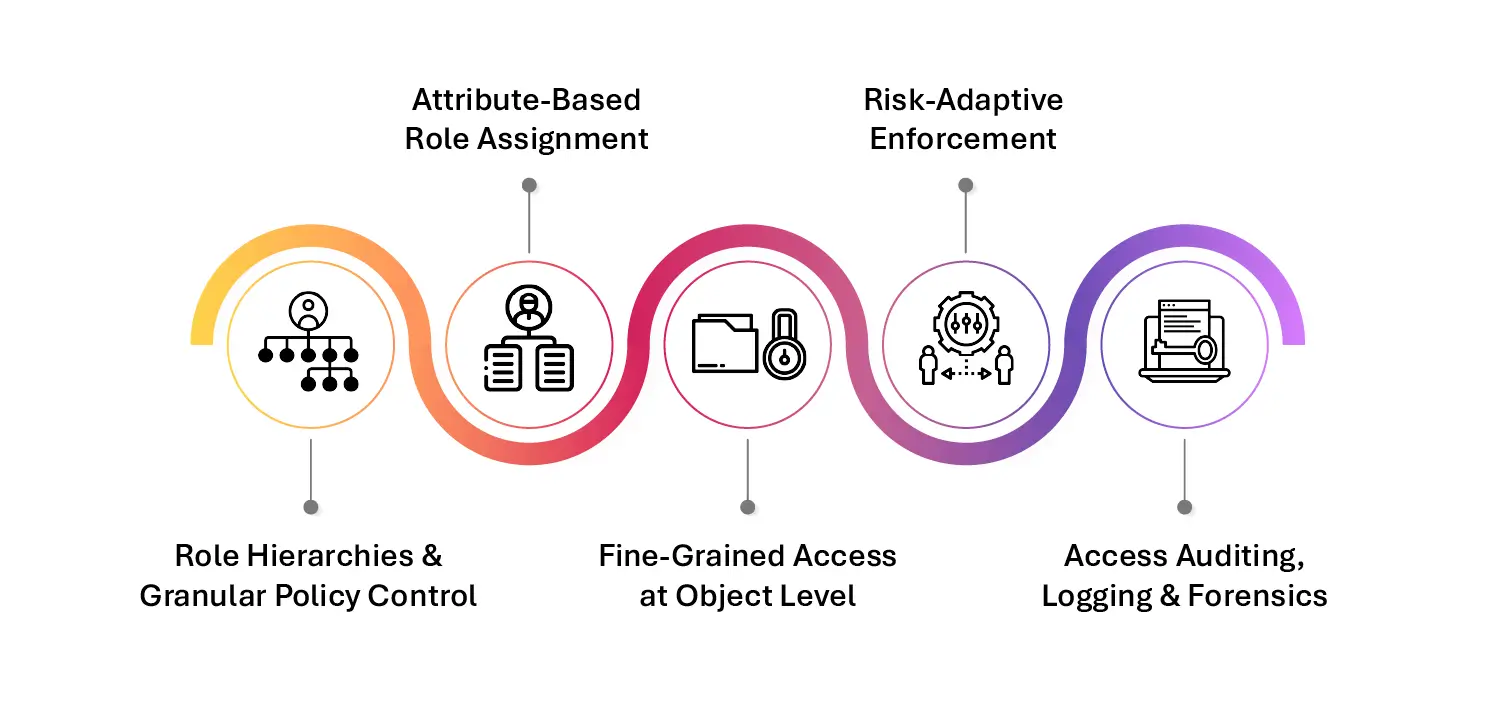
- Role Hierarchies and Granular Policy Control: RBAC supports layered access structures, such as Viewer, Editor, Admin—each inheriting permissions from the previous tier while extending them as needed. This enables nuanced delegation of authority without duplicating policies.
- Attribute-Based Role Assignment (ABAC Hybridization): Modern RBAC implementations integrate with ABAC (Attribute-Based Access Control), dynamically assigning roles based on user metadata, using systems like LDAP, Active Directory, or Azure AD.
- Fine-Grained Access at Object Level: Whether it’s access to a folder, a document, a specific database table, or even a metadata tag, RBAC systems can enforce policies down to the most granular level. This is critical when managing unstructured data across hybrid environments.
- Risk-Adaptive Enforcement: Some next-gen RBAC models integrate behavioral analytics, time-based access windows, and contextual factors (like unusual login locations) to dynamically elevate or restrict access.
- Access Auditing, Logging & Forensics: RBAC systems log every access attempt—successful or denied—along with timestamps, IP addresses, and user details. These logs are critical for incident investigation, legal defense, and demonstrating ongoing compliance.
How It Works
RBAC is governed by three primary rules:
- Role Assignment: A user must be assigned one or more roles.
- Role Authorization: Each role must be authorized to perform specific operations on resources.
- Permission Association: Roles are mapped to specific access rights, such as read, write, delete, or modify, on defined assets.
The Next Frontier in Access Management
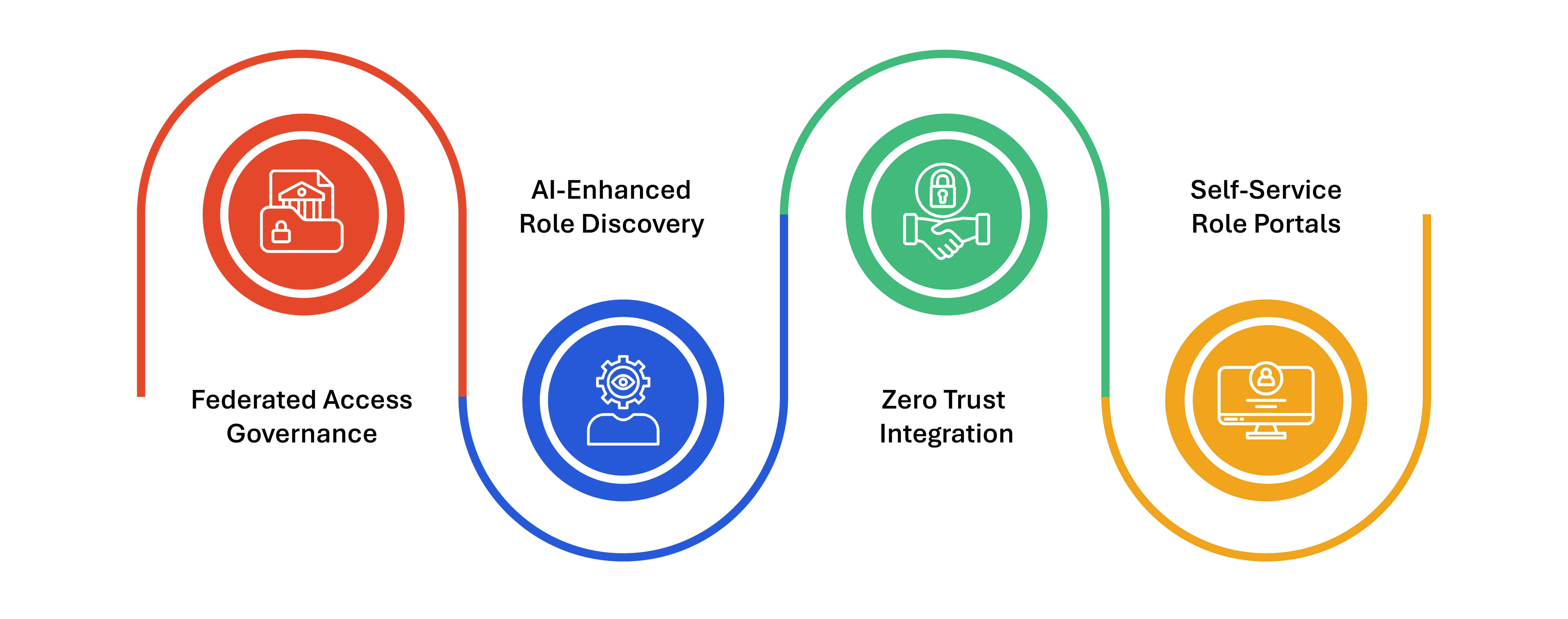
RBAC is rapidly evolving to keep pace with real-time risk, AI, and the need for cross-domain collaboration.
- Federated Access Governance: As organizations adopt hybrid and multi-cloud ecosystems, RBAC systems are expanding to unify access policies across AWS, Azure, GCP, and on-prem systems. This ensures consistent enforcement of rules enterprise-wide.
- AI-Enhanced Role Discovery: AI models are now being used to analyze user behavior, access history, and peer comparisons to recommend optimized role assignments and flag permission anomalies.
- Zero Trust Integration: RBAC is becoming a core component of Zero Trust security models. In Zero Trust, access is never implicitly granted, and RBAC helps ensure it is continuously verified, risk-scored, and context-aware.
- Self-Service Role Portals: Progressive enterprises are implementing self-service platforms where employees can request temporary access to specific roles, which are approved or denied based on dynamic policies and risk assessments.
RBAC in the Context of Unstructured Data
One of the biggest challenges today is securing unstructured data, which accounts for over 80% of enterprise data. Files stored across endpoints, shared drives, collaboration tools, and cloud repositories are often left over-permissioned and under-monitored.
Modern RBAC platforms—like those embedded in self-service data management tools—apply access control policies at the file, metadata, or content level. Combined with role-based visibility and automated re-permissioning, organizations can ensure AI training data, PII, PHI, and IP remain accessible only to authorized personnel.
Role-Based Access Control is more than just a security protocol—it’s a foundational principle for digital trust, ethical AI, and operational resilience. In today’s high-stakes data environment, where every file, query, or access request can carry regulatory, financial, or reputational risk, RBAC ensures that access is earned, enforced, and evolvable.
Whether you’re governing data across global regions, enabling secure AI development, or preparing for your next audit, RBAC is the silent guardian ensuring your data stays in the right hands, every time.
Getting Started with Data Dynamics:
- Learn about Unstructured Data Management
- Schedule a demo with our team
- Read the latest blog: AI Is Only as Secure as the Data You Feed It. Is Yours Truly Ready?






