Since the early 2000s, the healthcare industry has undergone a rapid transformation. The capacity in which the healthcare industry operates is no less than a Sci-fi movie! Just over ten years ago, the Human Genome Project completed mapping human DNA, and now individuals can perform at-home genetic tests at nominal costs. This transformation has led to a humongous amount of data and with the adoption of the latest innovative technologies, it’s predicted to increase by manifolds.
Previously, manila folders were used to document the health records, but now many patients and their families can access their health records online. In fact, the COVID-19 pandemic and its need for social distancing have encouraged and increased the online availability of healthcare apps. These online apps are conveniently utilized by patients to consult a doctor at any given time with just a click and along with loads of online data sharing.
HITECH (Health Information Technology for Economic and Clinical Health) bill was passed in 2009 as part of the recovery act in support of the benefits of digitalization in healthcare. Healthcare providers are encouraged to use electronic health records (EHRs) by the HITECH Act in which HIEs (Health Information Exchanges) benefit patients and the data can be shared to help doctors. This also means that the EHRs are shared between multiple providers such as the diagnostic labs, the doctors, the patients, and more making it vulnerable to online data theft.
Although it’s great that we are experiencing and gaining several benefits from the technological advancements in the healthcare industry, it also serves some challenges. Protection of the patient’s data is one of the prime areas of challenge for the healthcare industry as with growing technological advancements it’s also growing by greater manifolds. Did you know the healthcare industry experiences the highest number of data breaches as compared to any other industry? What’s more alarming is that according to the HIPAA Journal in 2023, with the healthcare sector accounting for 45% of all reported data breaches, in the first half of 2023 alone, there were 308 healthcare data breaches reported to the U.S. Department of Health and Human Services (HHS), affecting over 40 million individuals. The implications of this trend are alarming, as unauthorized access to sensitive healthcare information can have severe consequences for individuals and healthcare organizations. Breaches can result in compromised medical records, financial losses, and even identity theft.
Several healthcare records were exposed and potentially stolen in the two biggest healthcare data breaches. In July 2023, HCA Healthcare, one of the largest healthcare providers in the United States, suffered a data breach that compromised the records of 11.27 million individuals. The breach was caused by a sophisticated ransomware attack that exploited a vulnerability in the company’s IT systems. Another largest breach was reported by MCNA Dental, a dental insurance company in August 2023, reported a data breach that affected 8.8 million individuals. The breach was caused by a phishing attack that tricked employees into clicking on a malicious link, which gave hackers access to the company’s network.
IDC estimates that 80% of medical data remains untapped and unstructured after its creation. The data types under this category comprise typed and written text, radiological images, pathology slides, video, audio, streaming device data, PDF files, faxes, PowerPoint slides, and emails. Even the healthcare organizations that integrated IT and electronic health records (EHRs) to enhance interoperability now sit on mountains of unstructured data that are hard to find, organize, process, or use. Most high-profile data breaches involve the release of unstructured information containing personal information such as addresses, names, account information, and so forth.
Hence the question arises: What steps can be taken to address these challenges?
HIPAA is one of the first regulations concerning data privacy in the history of data access governance. Health Insurance Portability and Accountability Act (HIPAA) was passed in 1996 and is an outlined set of rules that healthcare organizations must follow and implement to protect PHI. Health providers were required to share information under HIPAA, but they also had to get the informed consent of patients. Organizations that handle PHI must have specific security, network, and process measures in place to protect this information, which is regulated by the Department of Health and Human Services (HHS) and the Office for Civil Rights (OCR). HIPAA’s most important aspect has little to do with technical concerns such as encryption, backup, logging, or any other aspect of securing data. What’s important is what happens when ePHI is breached or disclosed to an unauthorized individual. HIPAA Privacy Rule defines a breach as the unauthorized exposure of ePHI or its disclosure. In 2013, the HITECH Act amended the breach rules.
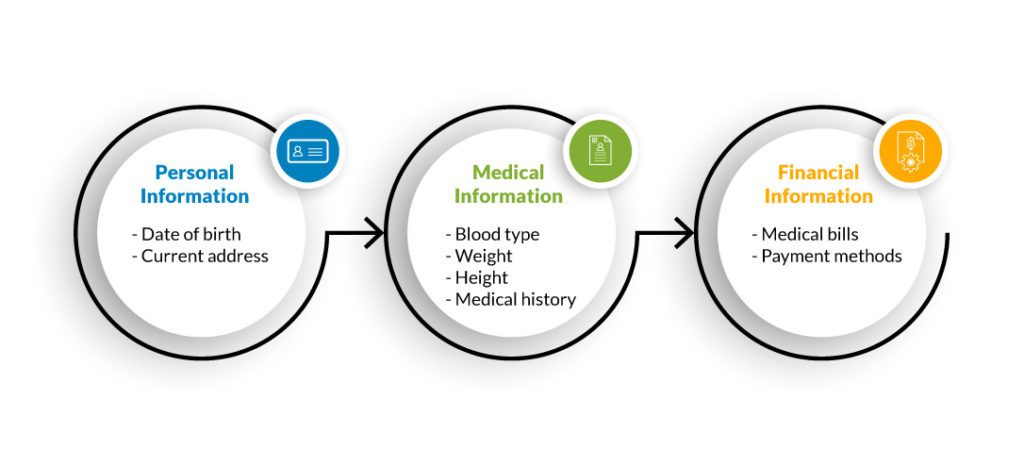
Which types of data are protected by HIPAA? HIPAA divides PHI into three categories, each with equal protection.
The covered entity must sign an agreement while hiring an employee or contractor that specifies what kind of PHI this employee or contractor has access to.
According to HIPAA, PHI is any individually identifiable information pertaining to the past, present, or future health status of an individual and capturing the details related to healthcare services, payment of healthcare services, or the operation of healthcare services (PHI used in healthcare business activities).
How important is HIPAA compliance for all organizations?
In addition to protecting health insurance coverage for workers who lose or change jobs, HIPAA also reduces healthcare costs by standardizing the electronic transmission of administrative and financial data. Those businesses that are covered entities, business associates, and/or handling personal health information must be HIPAA-compliant and strictly follow HIPAA guidelines. The requirements apply to health plans and providers, as well as business associates, such as law firms, attorneys, accountants, insurance agents, consultants, and advisors. Often, these companies perform tasks that require access to patient data, making them equally liable for meeting the HIPAA regulations and rules.
ePHI is considered highly valuable and should be treated with extreme caution by any business collecting, sharing, or receiving it. Records on paper and conversations between staff and patients qualify under HIPAA compliance law as well. Despite its focus on patients, HIPAA also covers the PHI of medical staff.
Another question that pops up is for the people who do business several miles away from America, does it matter to them as well. According to HIPAA security standards, when doing business with American healthcare organizations, those hospital systems, medical practices, and clinics will need to know that you or your employees will be able to protect PHI.
HIPAA consists of five main components:
To help keep patients’ medical information safe, it has security provisions and data privacy provisions. Overall, there are five titles, or sections, in the act:
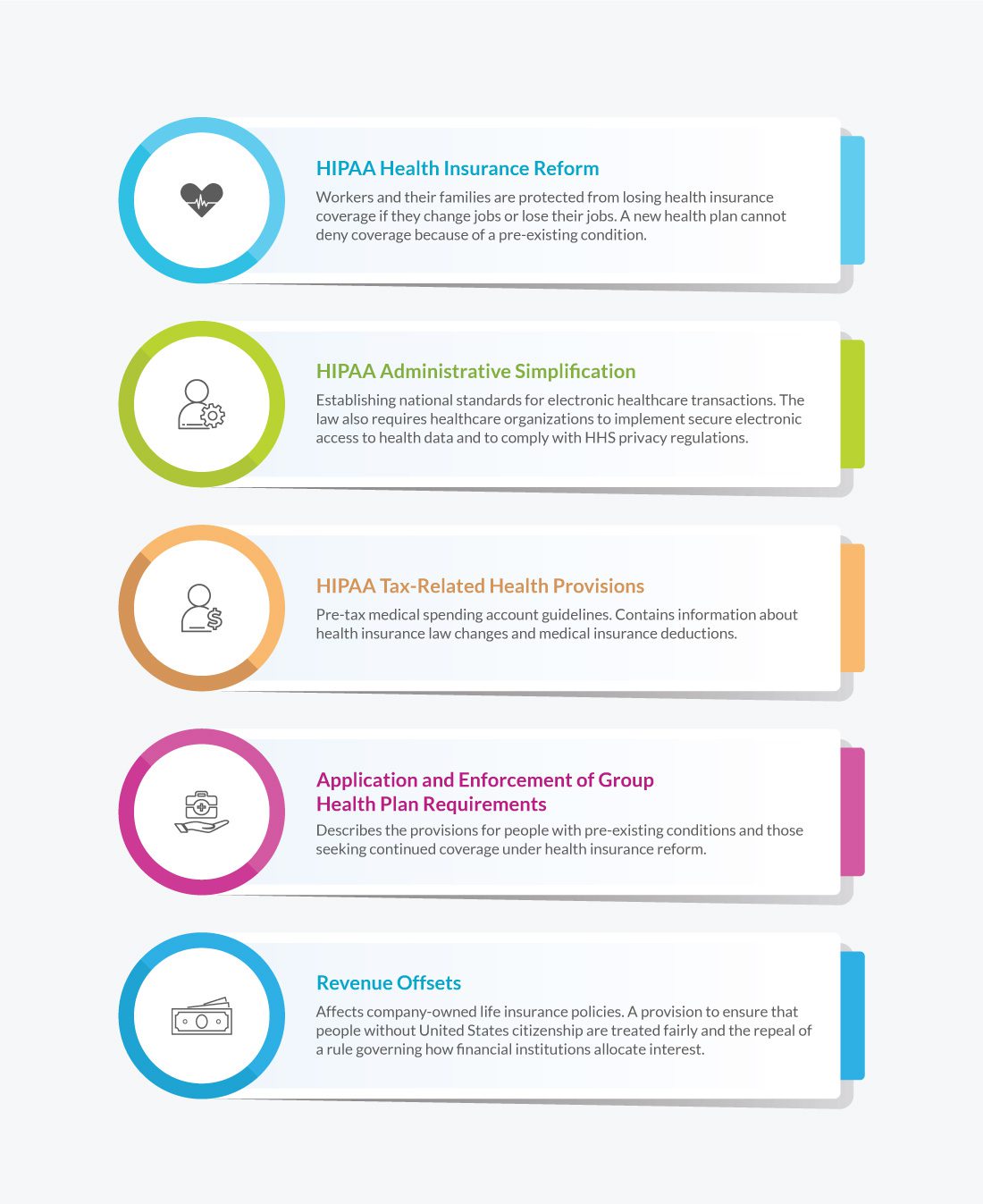
HIPAA compliance in IT refers to Title II, also known as the administrative simplification provisions.
HIPAA violations are punishable
For HIPAA violations, the OCR of the Department of Health and Human Services and state attorneys general can impose penalties. A violation of HIPAA laws is subject to varying penalties, depending on how much knowledge a covered entity had of the violation. In addition to considering several “general factors,” the OCR considers the seriousness of the HIPAA violation when determining the penalty. There are four categories of penalties:
- Tier 1: The covered entity was unaware of this violation and couldn’t have avoided it even if reasonable care had been taken to comply with HIPAA Rules.
- Tier 2: Despite a reasonable amount of care, the covered entity was not able to avoid a violation. (but was not willfully negligent)
- Tier 3: An act of negligence that results in a violation of HIPAA Rules, when attempts have been made to rectify the violation.
- Tier 4: There has been no attempt to correct a violation of HIPAA Rules which constitutes willful neglect.
HIPAA penalties are separate for each type of violation. OCR is responsible for determining the appropriate range of financial penalties. When determining penalties, OCR considers several factors, including how long the violation persisted and how many people were affected by it. The willingness of an organization to cooperate with an OCR investigation is also considered.
- Tier 1: There is a minimum fine of $100 per violation up to $50,000
- Tier 2: Fine between $1,000 to $50,000 per violation
- Tier 3: Up to $50,000 fine per violation with a minimum of $10,000
- Tier 4: There is a $50,000 minimum fine for each offense
HIPAA-covered entities and business associates that violate HIPAA Rules may face civil penalties. For example, wrongful disclosures of patient information with the intent to harm are criminal HIPAA violations. As HIPAA compliances are updating rapidly, it can sometimes be challenging to comply with them effectively.
Here are the top HIPAA violations:
- According to the HIPAA Privacy Rule, patients can access their medical records and obtain copies upon request. Patient records can be checked for errors and shared with other entities and individuals. HIPAA violations include denying patients copies of their medical records, overcharging for copies, or failing to provide those records within 30 days.
- Another common HIPAA violation is the failure to enter into a HIPAA-compliant business associate agreement with every vendor who is given access to PHI.
- Unencrypted data – Encrypted data can be added during loss and theft of devices to add extra security. Even though encryption isn’t mandatory under HIPAA, it provides additional security, especially when a password-protected device containing PHI data is somehow hacked. As an alternative to encryption, the company can use another method to protect ePHI and PHI data.
- The Privacy Rule prohibits access to a patient’s health records for anything other than treatment, payment, or healthcare operations.
- Data disclosures that are improper and not permitted are one of the most common violations of HIPAA.
- Under the HIPAA Security Rule, covered entities and their business associates must limit access to ePHI to authorized individuals.
- The failure to perform an enterprise-wide risk analysis is one of the HIPAA violations that can result in a financial penalty.
- Failure to notify the public of a data breach within 60 days.
- Identified risks must then be managed in a reasonable time frame.
What’s the solution? How must organizations be HIPAA ready and avoid violation of compliance?
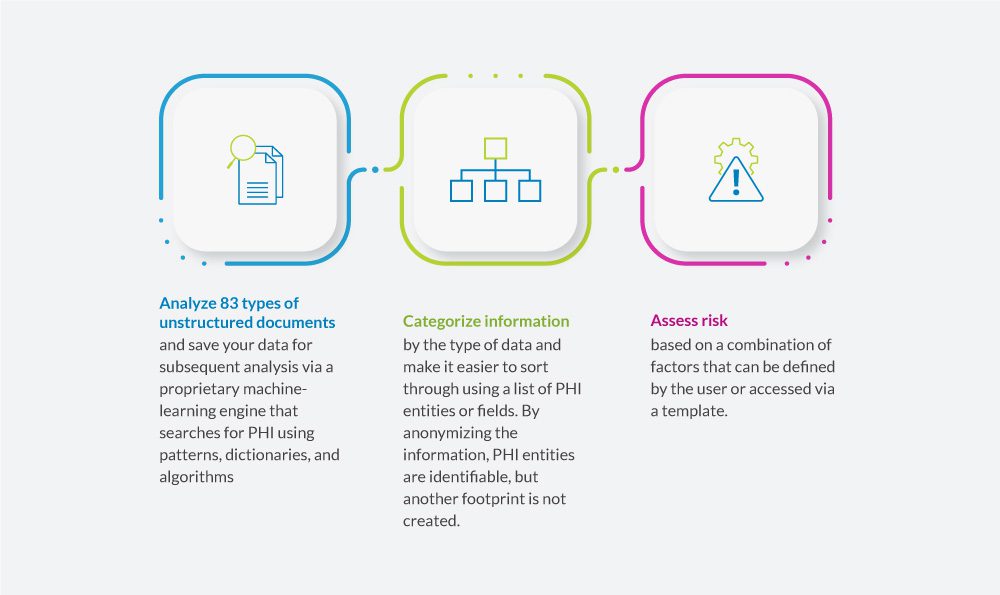
Data Dynamics’ Insight Analytix software provides a one-stop solution for filtering data intelligently based on criteria that are defined in PHI. In terms of addressing the risks associated with sensitive data, it bridges a gap that is present in the market. In addition, it provides a mechanism to trigger automated remediation with the provision of securing data from unwarranted access. Furthermore, the remediation analyst can further quarantine the data to locate sensitive files in more securely accessible and user-controlled locations.
With Insight AnalytiX, organizations can:
HIPAA violations can go undetected for months or even years. The longer they persist, the larger the penalty. Therefore, HIPAA-covered entities must conduct regular HIPAA compliance reviews to ensure that HIPAA violations are detected and corrected before they are identified by regulators.
For more information, visit – https://www.datadynamicsinc.com/insight-analytix/
Contact us solutions@datdyn.com or click here to request a demo.






