- The finance industry’s digital transformation has been impressive, with over 90% of financial institutions adopting some form of FinTech solutions.
- Several notable companies have experienced significant data breaches in the finance industry, serving as cautionary tales for the importance of robust cybersecurity measures.
- To stay ahead of cybercriminals, financial organizations must anticipate future cybersecurity trends and adopt cutting-edge technologies to strengthen their defenses.
- Financial institutions that prioritize data literacy can establish comprehensive and effective protocols to handle cyber attacks swiftly and efficiently.
The finance industry has witnessed an impressive digital transformation, with a staggering 90% of financial institutions embracing FinTech solutions. This shift has undoubtedly made life more convenient for consumers, as evidenced by the 65% of adults regularly using online banking and 81% utilizing mobile banking applications. Talk about keeping up with the times!
But amidst all the tech-savviness and convenience, there’s a lurking concern: cyber attacks. Yep, you heard that right. With an increased reliance on technology, financial institutions have become the prime targets for cybercriminals, making up a whopping 35% of all data breaches in 2022. And guess what’s scarier? Human error is the culprit behind a whopping 95% of these breaches. Ouch!
The impact of these attacks can be devastating. In fact, a startling 60% of small businesses that fall victim to a cyber attack end up shutting their doors within just six months. Now, that’s not the kind of stats anyone wants to be a part of!
As the threat landscape continues to evolve, investing in cutting-edge security solutions to protect sensitive financial enterprise data becomes a non-negotiable aspect of the finance industry’s growth and success. Robust cybersecurity measures and continuous employee training and awareness are nothing short of essential. After all, the world of finance is all about trust and reliability, and cybersecurity is the fortress that keeps everything intact.
Welcome to this blog, where we’re diving into the nitty-gritty of the five biggest data breaches that rocked 2023! We’ll uncover the causes behind these unfortunate incidents, explore the mitigation plans that were put into action, and, most importantly, extract key learnings to help us proactively manage risks in the future. So, fasten your seatbelts as we take a deep dive into the world of cybersecurity, learning from past challenges to build a safer and more resilient digital landscape.
Top 5 Cyber Breaches in the Finance Industry and Their Key Learnings
Several notable BFSI companies have experienced significant data breaches in 2023, serving as cautionary tales for the importance of robust cybersecurity measures. Here are the top 5:

Cause: The breach occurred due to a security vulnerability in MOVEit’s software, which allowed hackers to infiltrate the systems of several prominent companies. Among the affected organizations were industry giants such as Shell, Siemens Energy, Schneider Electric, as well as financial institutions like First Merchants Bank and City National Bank. The hackers exploited this weakness to gain unauthorized access to sensitive and confidential data, putting the privacy of countless individuals and businesses at risk.
Mitigation Strategy: Once the security vulnerability was identified, MOVEit took immediate action and swiftly patched the software to address the issue. This response helped prevent further exploitation of the vulnerability, demonstrating the importance of prompt and proactive software updates in maintaining a secure environment. In addition, the companies impacted by the breach took proactive steps to mitigate the potential fallout. They diligently notified their customers about the incident, ensuring transparency and allowing users to take necessary precautions to safeguard their information. Moreover, these organizations went the extra mile by offering credit monitoring services to the affected individuals, aiding in early detection of any suspicious activities related to their personal data.
Key learnings:
- Timely Software Updates and Vulnerability Management: The Moveit data breach highlights the critical importance of promptly applying software updates and managing vulnerabilities. Failing to address known security weaknesses can leave systems exposed to potential cyberattacks. Regularly updating software with the latest patches is essential in maintaining a secure digital environment.
- Robust Incident Response Planning: A well-prepared incident response plan is invaluable when dealing with a data breach. Moveit’s swift action in patching the software once the vulnerability was identified is commendable. Having a comprehensive incident response plan enables organizations to detect, contain, and mitigate breaches efficiently, minimizing potential damage and ensuring a quicker recovery process.
- Transparency and Customer Communication: In the aftermath of a data breach, transparent communication with customers is vital. Affected companies, such as Shell, Siemens Energy, Schneider Electric, First Merchants Bank, and City National Bank, took responsible steps to notify their customers about the incident. This level of transparency builds trust and allows customers to take necessary precautions to protect their data.

Cause: The Clop ransomware group carried out a targeted attack on several high-profile financial institutions, including Bank of America, Wells Fargo, and JPMorgan Chase. These cybercriminals exploited vulnerabilities in the companies’ systems, gaining access to their networks and swiftly encrypting sensitive data. To make matters worse, they demanded a hefty ransom payment in exchange for decrypting the hijacked data, putting the affected institutions in a difficult and precarious position.
Mitigation Strategy: The financial institutions that fell victim to the Clop ransomware attack managed to show resilience and resourcefulness in the face of the crisis. Thankfully, they were able to recover a significant portion of their encrypted data without succumbing to the attackers’ demands for ransom payments. However, it’s important to note that despite their ability to recover data, the attack still caused significant disruption to the day-to-day operations of these institutions.
Key learnings:
- Heightened Preparedness Against Ransomware Threats: The Clop ransomware attack serves as a wake-up call to businesses about the escalating ransomware threat landscape. Organizations must proactively assess their vulnerabilities and prepare comprehensive defense strategies to thwart potential attacks. Staying vigilant and continuously updating cybersecurity measures are essential to stay ahead of evolving ransomware tactics.
- The Value of Data Protection and Resilience: The Clop attack highlights the immense value of robust data protection and resilience measures. Ensuring regular data backups and secure storage systems can mitigate the impact of ransomware incidents. Organizations that prioritize data protection can recover their critical information without giving in to ransom demands, maintaining business continuity and customer trust.
- Collaborative Threat Intelligence Sharing: In the face of increasingly sophisticated cyber threats like the Clop ransomware attack, collaboration and information sharing among organizations become crucial. Establishing alliances to share threat intelligence allows businesses to stay informed about emerging ransomware trends and defensive strategies. This collective knowledge empowers organizations to strengthen their cybersecurity postures collectively.

Cause: The Capital One data breach was initiated when a cleverly crafted phishing email tricked an employee into unwittingly providing their login credentials. Armed with this sensitive information, the attackers gained unauthorized access to the company’s network, compromising valuable data such as customer names, credit card numbers, and Social Security numbers.
Mitigation: In response to the breach, Capital One swiftly took action to mitigate the impact on affected customers. They offered free credit monitoring services to those whose data had been compromised. Additionally, the company diligently reviewed and updated its security policies and procedures to enhance defenses against future breaches.
Key learnings:
- Heightened Focus on Multi-Factor Authentication (MFA): The Capital One data breach serves as a stark reminder of the importance of implementing robust multi-factor authentication measures. Enforcing MFA adds an additional layer of security, requiring attackers to bypass multiple verification steps even if they manage to obtain login credentials through phishing attempts. By embracing MFA, organizations can significantly reduce the risk of unauthorized access to sensitive data.
- Continuous Improvement of Security Policies and Procedures: The incident underscores the significance of regularly reviewing and enhancing security policies and procedures. Cyber threats are constantly evolving, and organizations must adapt their defenses accordingly. Capital One’s swift response in revisiting and strengthening its security measures demonstrates the importance of proactive and continuous improvement to stay ahead of potential breaches.
- Rigorous Phishing Awareness Training: The Capital One breach highlights the necessity of comprehensive phishing awareness training for all employees. Educating staff about the tactics employed by cybercriminals in phishing attacks empowers them to recognize and avoid potential threats. Regular training sessions instill a security-first mindset, reducing the likelihood of employees falling prey to deceptive phishing emails.

Cause: The Equifax data breach occurred when hackers exploited a security vulnerability on the company’s website. Through this loophole, they gained unauthorized access to the personal and financial data of over 147 million customers. The compromised data included highly sensitive information such as names, Social Security numbers, and credit card numbers.
Mitigation: In response to the breach, Equifax took swift action to mitigate the impact on affected customers. The company provided free credit monitoring services to those whose data had been compromised. Additionally, Equifax proactively reviewed and improved its security policies and procedures to bolster its defenses against potential future breaches.
Key learnings:
- Heightened Emphasis on Data Privacy and Protection: The Equifax data breach highlights the critical importance of prioritizing data privacy and protection. Organizations that handle sensitive customer information must implement robust security measures, including encryption and access controls, to safeguard data from potential cyber threats. Proactively securing customer data ensures greater trust and confidence in the organization’s ability to protect its customers’ sensitive information.
- Enhanced Vendor and Third-Party Risk Management: The Equifax breach underscores the significance of implementing robust vendor and third-party risk management practices. Often, cyber attackers exploit vulnerabilities in third-party systems to gain unauthorized access to valuable data. Conducting thorough security assessments of vendors and ensuring compliance with cybersecurity standards can help mitigate the risk of breaches originating from external sources.
- Transparent and Timely Customer Communication: Timely and transparent communication with affected customers is crucial in the wake of a data breach. The Equifax incident demonstrated the importance of promptly notifying customers about the breach and its potential impact on their data. Clear and concise communication helps customers take necessary precautions, such as monitoring their accounts and taking advantage of offered credit monitoring services, fostering trust and goodwill amidst a challenging situation.

Cause: The breach occurred due to a security vulnerability in Heartland Payment Systems’ payment processing system. Cybercriminals capitalized on this weakness, gaining unauthorized access to credit card data belonging to more than 130 million customers.
Mitigation: In response to the breach, Heartland Payment Systems took proactive measures to mitigate its impact on affected customers. The company offered free credit monitoring services to help customers monitor and detect any unusual activities related to their credit cards. Additionally, Heartland Payment Systems diligently reviewed and strengthened its security policies and procedures to fortify its defenses against future breaches.
Key learnings:
- Emphasizing Industry Compliance Standards: The Heartland Payment Systems attack highlights the significance of adhering to industry compliance standards and regulations. Payment processors and financial institutions must ensure strict compliance with Payment Card Industry Data Security Standard (PCI DSS) requirements to safeguard customers’ credit card data. Meeting these standards can significantly reduce the risk of data breaches and protect the trust of customers.
- Swift Detection and Incident Response: Incident response is a crucial aspect of cybersecurity. Detecting breaches promptly and responding swiftly can significantly minimize the potential damage caused by cyberattacks. Having an effective incident response plan in place ensures that organizations can take immediate action to contain and mitigate the impact of breaches.
- Proactive Security Assessments: Regular security assessments are indispensable in identifying and addressing vulnerabilities within a system. Conducting periodic security assessments allows organizations to stay ahead of potential threats, remediate weaknesses, and maintain a vigilant defense posture.
Future Outlook: Anticipating Cybersecurity Trends in the Finance Industry
The future of cybersecurity threats is shaped by rapid advancements in technology and the evolving cyber landscape. While it’s challenging to predict every specific threat, some potential trends and emerging threats that may impact cybersecurity in the future include:
- Artificial Intelligence (AI) and Machine Learning (ML) Threats: Cybercriminals are increasingly leveraging AI and ML to create more sophisticated and targeted attacks. AI-powered malware, chatbots for social engineering, and automated evasion techniques could become prevalent in future cyber threats.
- Internet of Things (IoT) Vulnerabilities: The proliferation of IoT devices introduces new attack surfaces. Vulnerabilities in smart home devices, connected medical devices, and industrial IoT systems could be exploited by cybercriminals to launch large-scale attacks or gain unauthorized access to critical infrastructure.
- 5G Network Exploitation: As 5G networks become widespread, they offer increased bandwidth and lower latency, but they also introduce new security challenges. Threats related to 5G network vulnerabilities, such as increased Distributed Denial of Service (DDoS) attacks, may emerge.
- Supply Chain Attacks: Cyber attackers may focus on infiltrating the supply chain to target software and hardware vendors, compromising products before they even reach end-users. Supply chain attacks could lead to widespread data breaches and disruptions.
- Quantum Computing Threats: While quantum computing promises revolutionary advancements, it also poses risks to current encryption algorithms. Cybersecurity protocols may need to adapt to the quantum computing era to ensure data remains secure.
- Ransomware Evolution: Ransomware attacks are likely to evolve with more targeted and customized attacks, incorporating techniques like “double extortion” (threatening to leak stolen data) to increase the pressure on victims.
- Deepfakes and Identity Fraud: The use of deepfake technology to create realistic but fake audio and video content could lead to new forms of identity fraud and social engineering attacks.
- Cloud Security Challenges: As more data and services move to the cloud, securing cloud environments becomes increasingly critical. Misconfigurations, insecure APIs, and shared responsibility models may expose cloud services to breaches.
- Mobile and Remote Workforce Risks: The rise of remote work and mobile devices opens up new avenues for cyber threats. Attacks targeting mobile devices, VPNs, and unsecured home networks may increase.
- Cyberwarfare and Nation-State Attacks: Nation-states may continue to use cyber tactics for espionage, political disruption, and economic warfare. Critical infrastructure, election systems, and communication networks may be targeted.
To stay ahead of cybercriminals, financial organizations must adopt cutting-edge technologies to strengthen their defenses. Here are some key technologies to consider for the future outlook of cybersecurity in the finance industry.
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML play pivotal roles in cybersecurity by enabling real-time threat detection and response. These technologies can analyze vast amounts of data, identify patterns, and detect anomalies, helping financial institutions stay ahead of sophisticated cyber threats.
- Behavioral Biometrics: Behavioral biometrics utilize user behavior patterns, such as typing speed, mouse movements, and touchscreen gestures, to authenticate users. This technology can enhance security by continuously monitoring user interactions to identify potential unauthorized access or fraudulent activities.
- Zero Trust Architecture: Zero Trust is a security model that assumes no user or device should be inherently trusted. Instead, access is verified continuously based on various factors. Implementing Zero Trust architecture can significantly reduce the risk of lateral movement within networks and minimize the impact of potential breaches.
- Quantum-Resistant Cryptography: With the advent of quantum computing, traditional cryptographic methods could become vulnerable to attacks. Implementing quantum-resistant cryptography ensures data remains secure against future quantum threats.
- Cloud Security Solutions: As financial institutions increasingly move their operations to the cloud, implementing robust cloud security solutions is essential. Cloud Access Security Brokers (CASBs) and Secure Access Service Edge (SASE) platforms provide visibility and control over cloud applications and data, ensuring a secure cloud environment.
- Blockchain Technology: Blockchain’s decentralized nature and cryptographic features offer enhanced security for financial transactions and data storage. Implementing blockchain in financial systems can minimize the risk of data tampering and provide more transparent and secure transactions.
- Threat Intelligence Platforms: Threat intelligence platforms collect and analyze data from various sources to provide insights into emerging cyber threats. These platforms help financial institutions proactively address potential vulnerabilities and stay informed about the latest attack vectors.
- Security Orchestration, Automation, and Response (SOAR): SOAR platforms automate security processes and streamline incident response, enabling quicker and more efficient detection, containment, and remediation of cyber threats.
- User Behavior Analytics (UBA): UBA solutions analyze user behavior to detect anomalies and potential insider threats. These technologies help financial institutions identify suspicious activities and unauthorized access.
In today’s ever-evolving cyber risk landscape, staying ahead of sophisticated cyber threats is paramount for organizations across all sectors, especially in the finance industry. As technology advances and threat actors become more adept, it is crucial for businesses to adopt a proactive cybersecurity approach. One of the fundamental pillars of this approach is data literacy – equipping employees and stakeholders with the knowledge and skills to understand, interpret, and protect data effectively. It serves as the foundation for cultivating a culture of security awareness and proactive risk mitigation. This, combined with cutting-edge cybersecurity technologies, enables businesses in the finance industry to navigate the evolving risk landscape with greater confidence and resilience. Let’s find out how.
Data Literacy is the Key: 5 Strategies to Shield Financial Institutions from Cyber Attacks
Data literacy is the ability to effectively read, understand, interpret, and communicate with data. In the realm of cybersecurity, it goes beyond merely accessing and analyzing data; it involves comprehending its implications and leveraging it to make informed decisions. Its growing importance in cybersecurity is fueled by the escalating sophistication and prevalence of cyber threats. A report by IBM reveals the jaw-dropping average cost of a data breach in 2024, standing at $4.45 million! Given these high stakes, cultivating a data-literate culture within an organization is not a mere luxury but an absolute necessity in today’s cyber landscape. Here are the top five reasons why.
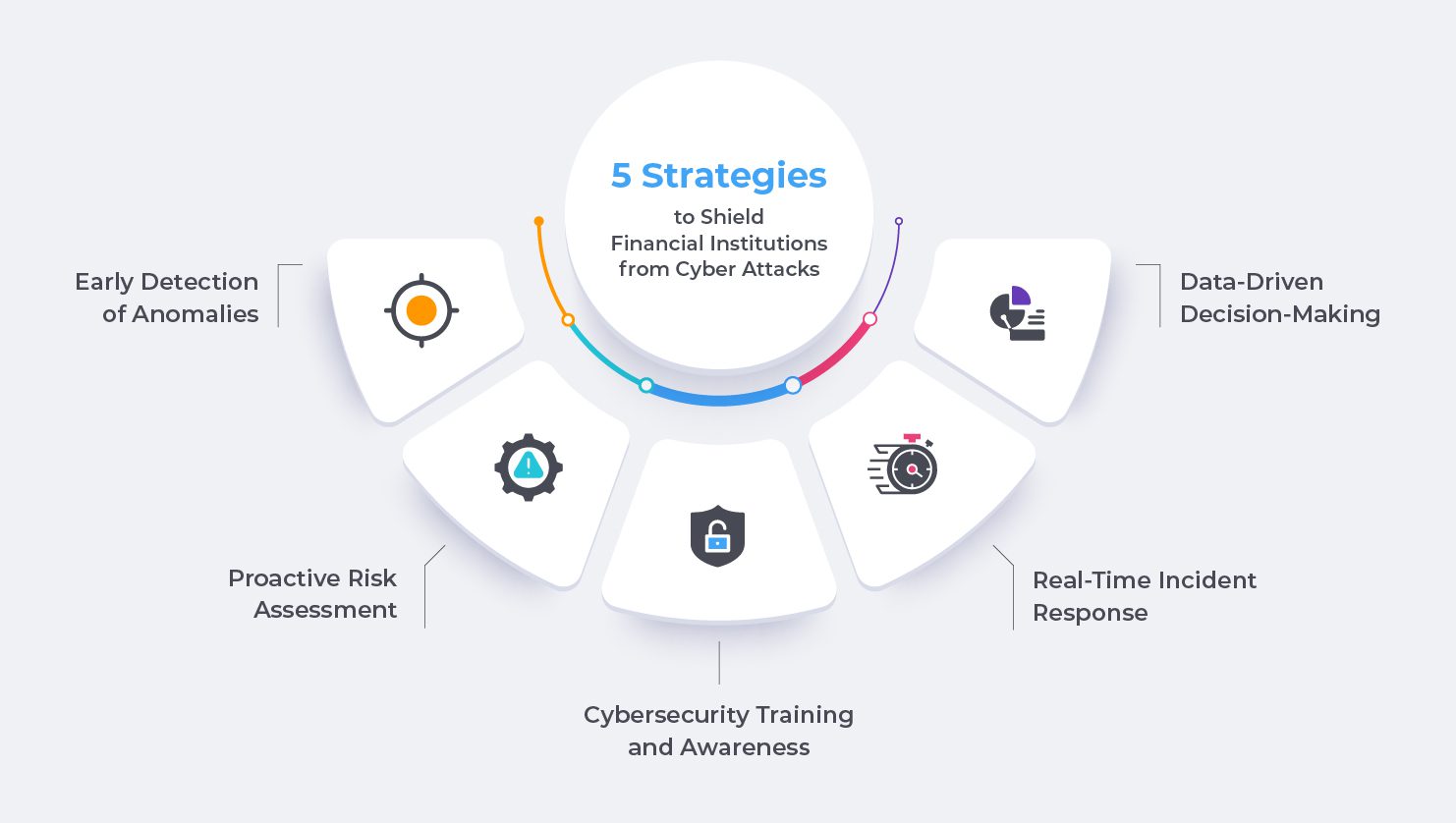
- Early Detection of Anomalies: Data-literate employees can efficiently analyze vast amounts of data to identify unusual patterns or activities which might indicate a cyber attack. For instance, if a company’s data analysts notice a sudden surge in failed login attempts from various locations, it could be an early sign of a potential brute-force attack. According to a study conducted by the Ponemon Institute, organizations that detect and contain a breach in less than 200 days can save up to $1.12 million in costs compared to those taking longer.
- Proactive Risk Assessment: Data-literate teams can perform robust risk assessments by analyzing historical cyber incidents and identifying vulnerabilities. They can use this information to implement preventive measures and improve the organization’s overall cybersecurity posture. A report by Accenture reveals that 83% of high-performing companies invest in technologies that improve proactive threat hunting and threat detection.
- Cybersecurity Training and Awareness: Data literacy goes hand in hand with cybersecurity training and awareness programs. When employees understand the value of data and its potential risks, they are more likely to adhere to security protocols and report suspicious activities promptly. A study by Wombat Security found that organizations that conduct regular security awareness training can reduce security-related risks by up to 70%.
- Real-Time Incident Response: Quick and effective incident response is crucial to minimizing the impact of cyberattacks. Data-literate teams can leverage real-time data analysis to detect and respond swiftly to threats. For example, when a financial institution notices unusual transaction patterns through their real-time data analytics platform, they can immediately trigger security protocols to prevent further damage.
- Data-Driven Decision-Making: In the realm of cybersecurity, every decision counts. Data literacy empowers organizations to make informed decisions based on data-driven insights. From investing in the right security technologies to prioritizing cybersecurity initiatives, data-driven decision-making ensures resources are allocated effectively. A report by MIT Sloan Management Review states that data-driven organizations are 3 times more likely to report significant improvements in decision-making.
The Data Dynamics Advantage
In today’s fast-paced and data-driven world, managing vast amounts of information can be a daunting task for organizations. With data scattered across various systems and departments, making sense of it and securing it can be overwhelming. However, unified data management offers a game-changing solution. By consolidating all data into a single platform and implementing standardized processes, enterprises can revolutionize their approach to data management and foster data literacy throughout the organization.
For over a decade, Data Dynamics has been working with global giants, helping them establish a data-literate culture. The company’s mission is to empower enterprises to achieve data democratization, enabling users of all technical backgrounds to access, understand, and gain valuable insights from unstructured data sprawls through its unified unstructured data management platform. This platform has garnered the trust of over 28 Fortune 100 organizations and encompasses four powerful modules – Data Analytics, Mobility, Security, and Compliance – all integrated within a single software. Employing a mix of automation, AI, ML, and blockchain technologies, organizations can ensure the security, privacy, and integrity of their data. The platform helps to identify and address vulnerabilities, bolstering the organization’s defenses against cyber threats. This proactive approach to data management not only safeguards against potential data breaches but also fosters a culture of data responsibility and protection within the organization.
With Data Dynamics, organizations can thrive in the digital landscape, knowing that their data is not only accessible and insightful but also well-protected and cyber-resilient.
To discover more about how Data Dynamics can help you build a cyber resilient data ecosystem, please visit www.datadynamicsinc.com or contact us at solutions@datdyn.com / (713)-491-4298 / +44-(20)-45520800.






