In our hyper connected and digital world, the financial services sector has become a magnet for cybercriminals, lured by the allure of exploiting vulnerabilities and seizing valuable assets. The rising tide of cyber risks and vulnerabilities in this industry has ignited deep concerns among professionals, regulators, and customers alike. And the fallout from these cyber attacks is nothing short of alarming, with potential financial losses, tarnished reputations, and the erosion of customer trust hanging in the balance. Join us on this captivating blog journey as we delve into the realm of cyber crimes in the BFSI sector. We will uncover their root causes, explore their most prominent catalysts, and equip you with five invaluable tips to construct a rock-solid security framework.
Unmasking the Shadows: Exploring the Cyber Threats Lurking
In the vast realm of the financial services sector, where fortunes are made and transactions occur at lightning speed, a dark underbelly thrives. It’s a world where cybercriminals lurk, seeking to exploit the immense wealth and sensitive data that flow through the veins of banks, insurance companies, investment firms, and payment processors. The numbers tell a chilling tale. In 2022 alone, this sector suffered over 3,500 data breaches, leading to the loss of a staggering 10 billion records. The consequences are not merely virtual; they have a real-world impact. The average cost of a data breach in the financial sector weighs in at a hefty $4.24 million.
These threats come in all shapes and sizes. Sophisticated malware attacks and data breaches aim to infiltrate the fortress of financial institutions, while social engineering tactics manipulate unsuspecting individuals into revealing valuable information. Let’s not forget about insider threats, where those on the inside pose a risk, intentionally or unknowingly. As technology advances, so too do the risks. The very innovations that enable groundbreaking financial services also introduce new avenues for exploitation, increasing the vulnerability of the sector. It’s a constant battle, a digital dance of wit and cunning.
But the impact of these cyber attacks extends far beyond the walls of individual institutions. A successful breach can send shockwaves through the financial systems, disrupting the delicate balance, and shaking market stability. Public confidence, once shaken, becomes a fragile thread, threatening the very integrity of the entire financial system. Compromised customer data exposes them to the looming specter of identity theft and financial fraud. It’s a breach of privacy and a betrayal of trust.
In fact, the Adobe 2022 Trust Report echoes these concerns. A staggering 84% of consumers emphasize the need for data safety, transparency, and control over how their data is used. For enterprises, it’s clear: to gain and maintain customer trust, these aspects are paramount.
Given these risks and the weight of these concerns, the financial services sector stands at a crossroads. It must prioritize cybersecurity like never before, fortifying its defenses, and safeguarding its valuable assets and sensitive information. The trust of customers hangs in the balance, and the sector must rise to the challenge, embracing the call for security, transparency, and control. In this interconnected world, where money and data intertwine, cybersecurity is not just a necessity—it’s a lifeline.
Distribution of cyber attacks on financial and insurance organizations worldwide from October 2021 to September 2022, by type
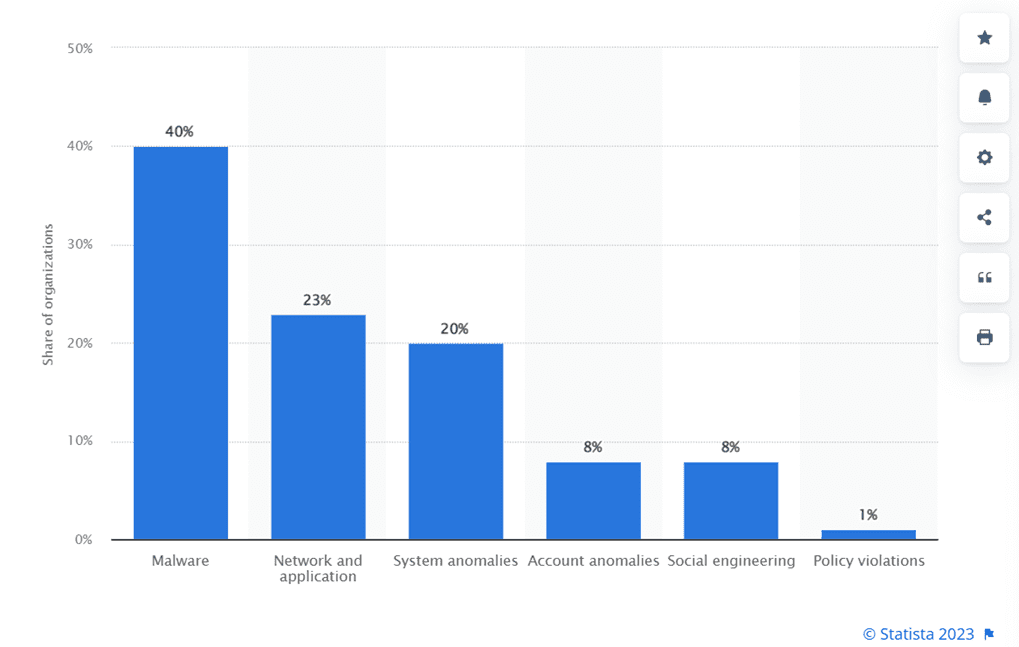
- Malware attacks: Malware, with its many sinister forms—viruses, worms, Trojans, ransomware, and spyware—seeks to infiltrate systems, causing mayhem and compromising precious data. How does it do it? Well, imagine unsuspecting users innocently opening an email attachment, visiting a seemingly harmless website, or downloading software from a compromised source. Little do they know, they’ve just invited this digital devil into their world.
Once inside, cybercriminals unleash the full power of their malicious software. They gain unauthorized access, disrupt operations, and plunder sensitive data. It’s like watching a virtual heist unfold. They infiltrate an institution’s network, quietly slipping past defenses, and then the real mischief begins. They pilfer valuable customer information, leaving a trail of stolen PII (personally identifiable information) and financial records in their wake. But that’s not all. They go even further, encrypting files and holding them hostage for a hefty ransom, leaving organizations in a state of panic and desperation. And just when you thought it couldn’t get worse, they turn unsuspecting devices into obedient minions, forming massive botnets to carry out large-scale attacks.
The aftermath of such breaches is nothing short of catastrophic. Financial losses pile up, reputations crumble, and legal consequences loom large. It’s a nightmare scenario that no organization or individual wants to experience.
- Network and application attacks: Network attacks are like cunning burglars that specialize in infiltrating computer networks, seeking out vulnerabilities to exploit for their nefarious purposes. Their aim? To gain unauthorized access, wreak havoc, and get their hands on sensitive information. These attacks come in all shapes and sizes, each with its own tricks up its sleeve. Picture a Distributed Denial of Service (DDoS) attack, where the network is bombarded with traffic until it collapses under the weight, leaving legitimate users stranded and frustrated. Sneaky packet sniffing attacks involve eavesdropping on network traffic, allowing attackers to intercept and analyze sensitive data passing through. And let’s not forget the notorious man-in-the-middle attacks, where attackers lurk in the shadows, secretly intercepting and tampering with communications between unsuspecting parties.
But wait, there’s more! Enter the realm of application attacks, where hackers set their sights on the vulnerabilities lurking within software applications. They exploit weaknesses, just like master lockpickers, aiming to gain unauthorized access, manipulate data, or launch even more sinister attacks. Imagine the treacherous cross-site scripting (XSS) attack, where attackers inject malicious code into web applications, lying in wait to steal sensitive data from unsuspecting users. And then there’s the devious SQL injection attack, where attackers manipulate databases by injecting malicious SQL code, bending the system to their wicked will.
It’s a constant battle against these cunning cybercriminals, but armed with knowledge and fortified defenses, we can outsmart and thwart their attempts to breach our networks and compromise our applications.
- System anomalies: System anomalies, oh, what a complex puzzle they present in the world of cybersecurity! These sneaky attacks occur when computer systems decide to go haywire, exhibiting behavior that catches us all off guard. It’s like finding hidden vulnerabilities that no one knew existed. These anomalies can arise from all sorts of mischief, like mischievous software bugs, misconfigurations, or even sassy clashes between different components of a system. And here’s the kicker: attackers are like mischievous maestros, expertly exploiting these anomalies to slip through the cracks, access restricted areas, meddle with precious data, and disrupt services.
The consequences? We’re talking about unauthorized access to top-secret information, the kind that gives us goosebumps. And don’t even get me started on the financial losses! System downtime, recovery and remediation costs, legal troubles, regulatory penalties—it’s a devastating blow to an organization’s hard-earned reputation.
- Account anomalies: Imagine a scenario where unauthorized individuals break into user accounts, causing chaos and wreaking havoc. These are what we call account anomalies, and they pose a serious threat to both individuals and organizations. There are various reasons behind these attacks, and one of the main culprits is weak or compromised passwords. It’s astonishing how many people use easily guessable passwords or recycle them across multiple accounts, practically rolling out the red carpet for attackers. To make matters worse, phishing attacks and credential leaks can result in compromised login information, which cybercriminals are more than happy to exploit for their nefarious purposes. Another major factor contributing to account anomalies is inadequate access controls and privileges. When access control policies are poorly defined or not enforced properly, unauthorized users can slip through the cracks and gain elevated privileges or access sensitive information. This opens the floodgates to unauthorized modifications, data breaches, and even those spine-chilling privilege escalation attacks. Let’s not forget about the danger lurking in outdated software and systems. When updates and security patches fall by the wayside, cyber attackers seize the opportunity to exploit vulnerabilities and gain unauthorized access to user accounts. It’s like leaving the front door wide open for them to stroll right in. Insider threats also play a significant role in account anomalies. Picture this: employees with access to systems, intentionally or unintentionally misusing their privileges, abusing their positions, or becoming unwitting pawns in the hands of attackers. The consequences can be disastrous, ranging from unauthorized data access and data exfiltration to full-blown sabotage.
Last but not least, enter the art of deception: social engineering tactics. These tricks of the trade, like phishing, spear-phishing, or social media manipulation, are the playgrounds of cybercriminals. They manipulate our psychology, tricking us into revealing sensitive information or granting access to our accounts without batting an eye.
- Policy Violations: Cybercrime stemming from policy violations highlights the crucial significance of adhering to organizational policies in upholding a robust digital ecosystem. When employees consciously or unconsciously disregard established policies and guidelines, they create lucrative opportunities for cybercriminals to exploit vulnerabilities and launch their malicious attacks. These policy violations manifest in various ways, including the unauthorized sharing of sensitive information, negligence in implementing essential security measures, or the usage of unapproved software and devices. Through their actions, individuals unknowingly weaken the overall security posture of the organization, jeopardizing valuable assets and sensitive data.
Several notable companies have experienced significant data breaches in the finance industry, serving as cautionary tales for the importance of robust cybersecurity measures. Here are the top 5:
- Equifax Data Breach (2017):
In one of the largest data breaches in history, Equifax, a leading credit reporting agency, fell victim to a cyber attack that compromised the personal information of approximately 147 million individuals. The attackers exploited a vulnerability in Equifax’s website software, gaining access to names, Social Security numbers, birth dates, and other sensitive data. The breach resulted in significant financial losses for Equifax, legal consequences, and severe reputational damage.
- Bangladesh Bank Heist (2016):
Cybercriminals attempted to steal nearly $1 billion from the Bangladesh Central Bank by exploiting vulnerabilities in the bank’s security systems. They gained access to the bank’s network and used fraudulent SWIFT messages to transfer funds to accounts in the Philippines. Although most of the fraudulent transfers were blocked, approximately $81 million was successfully stolen. The incident highlighted the vulnerability of financial institutions to sophisticated cyber attacks and the need for robust security controls and protocols.
- JPMorgan Chase Data Breach (2014):
JPMorgan Chase, one of the largest financial institutions globally, experienced a significant data breach that impacted approximately 76 million households and seven million small businesses. The attackers gained access to customer contact information, including names, addresses, email addresses, and phone numbers. While no financial information or Social Security numbers were compromised, the breach raised concerns about the security of customer data held by financial institutions and led to increased scrutiny of cybersecurity practices within the industry.
- NotPetya Ransomware Attack (2017):
NotPetya, a destructive ransomware attack, targeted financial institutions, among other industries, causing widespread disruption and financial losses. The malware infected networks through software update mechanisms and spread rapidly, encrypting critical data and rendering systems inoperable. NotPetya affected numerous financial institutions globally, resulting in halted operations, significant financial losses, and reputational damage. The incident highlighted the need for robust backup and recovery mechanisms, as well as the importance of timely patching and system updates.
- Carbanak Cybercrime Group (2013-present):
The Carbanak cybercrime group, active since 2013, targeted financial institutions worldwide, conducting sophisticated attacks with a focus on financial gain. The group employed various techniques, including spear-phishing, remote access trojans, and advanced malware, to gain access to financial networks and compromise systems. Carbanak stole hundreds of millions of dollars from banks, employing tactics such as ATM cash-out schemes, unauthorized transfers, and fraudulent SWIFT transactions. These attacks highlighted the evolving sophistication and persistence of cybercriminal groups targeting financial institutions.
These real-world case studies serve as stark reminders of the devastating consequences of cyber attacks on financial institutions. The incidents outlined above illustrate the tremendous financial losses, legal ramifications, damaged reputation, and shattered customer trust that can result from such breaches. They underscore the urgent need for comprehensive cybersecurity measures, including proactive threat detection, robust incident response plans, and a commitment to continuously improving defenses in the face of evolving cyber threats. Financial institutions must maintain a constant state of vigilance, investing in cutting-edge security technologies, and making cybersecurity a top priority to safeguard their operations and protect their customers from the potential fallout of cyber attacks.
Unstructured data: The root cause of security breaches
We reside in a world where every passing second adds to the avalanche of data, a treasure trove of potential insights. However, lurking beneath the surface lies a hidden menace: unstructured data. According to the experts at Gartner, a staggering 80 to 90 percent of the data generated today falls into this unstructured category, with a mere 12 percent receiving the analysis it deserves. But what exactly is unstructured data? It’s the elusive kind that eludes easy searchability and organization, encompassing handwritten notes, voice recordings, images, and other forms of media that resist easy classification. The result? Data sprawl—a state where crucial information exists, but without visibility or comprehension, rendering it useless.
Now, let’s focus on the financial sector, where unstructured data becomes an even more formidable adversary.
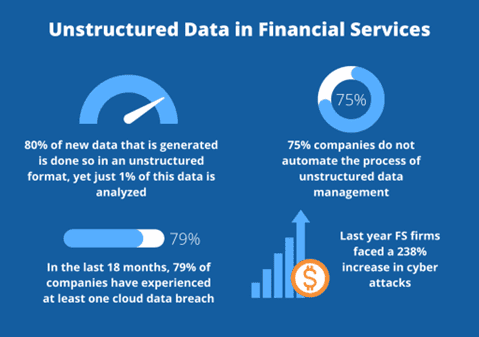
Banks and financial institutions churn out mountains of data daily, encompassing financial statements, loan agreements, audit reports, and sensitive treasures like images of checks or customer identification documents. While unstructured data presents a potential goldmine for invaluable insights and innovative breakthroughs, it also exposes enterprises to significant security challenges. The existence of unstructured data within the finance industry becomes a breeding ground for security breaches, amplifying the risks for multiple reasons. Here are the top 5:
1. In the vast labyrinth of unstructured data, organizations find themselves grappling with a multitude of challenges that put their sensitive information at risk. One of the foremost obstacles is the lack of visibility and control. Without a centralized approach to data management, tracking, monitoring, and securing sensitive information becomes an uphill battle. The absence of a clear line of sight opens the door for unauthorized access, data breaches, and a host of other malicious activities that thrive in the shadows.
2. Another hurdle lies in the realm of data classification. With the sheer volume and diversity of unstructured data, many enterprises find themselves struggling to classify it effectively. This classification process is crucial for prioritizing security efforts, yet without accurate categorization, sensitive data remains exposed, vulnerable to potential threats that may exploit this blind spot.
3. Insufficient access controls further compound the risks associated with unstructured data. Within its untamed realms lie troves of sensitive information that should be strictly limited to authorized personnel. However, without the enforcement of proper access controls, the risks of data leakage, insider threats, and unauthorized modifications soar, potentially leading to catastrophic consequences.
4. Enterprises often rely on data loss prevention (DLP) strategies to safeguard their information. However, when it comes to unstructured data, these ineffective DLP can prove to be a menace. Without robust content-aware monitoring and advanced analytics capabilities, DLP solutions struggle to effectively identify and protect sensitive information hidden within the vast expanse of unstructured data. This vulnerability leaves it exposed to unauthorized access or exfiltration, leaving organizations scrambling to contain the damage.
5. To compound matters, here comes compliance and regulatory gaps. Unstructured data frequently contains personally identifiable information (PII) and other sensitive data subject to strict regulatory requirements. Compliance with frameworks such as GDPR, PCI DSS, and industry-specific regulations becomes paramount. Failing to meet these obligations creates compliance and regulatory gaps, leaving organizations vulnerable to penalties, reputational damage, and legal consequences.
In this ever-evolving landscape, taming the untamed becomes paramount. Finding a balance between leveraging the potential of unstructured data while mitigating the security risks is the ultimate challenge that many enterprises face. Only by mastering this delicate dance can we ensure that our most valuable asset—data—remains a source of strength rather than a vulnerability waiting to be exploited.
4 Proven Strategies for Crafting an Ironclad Data Security Framework
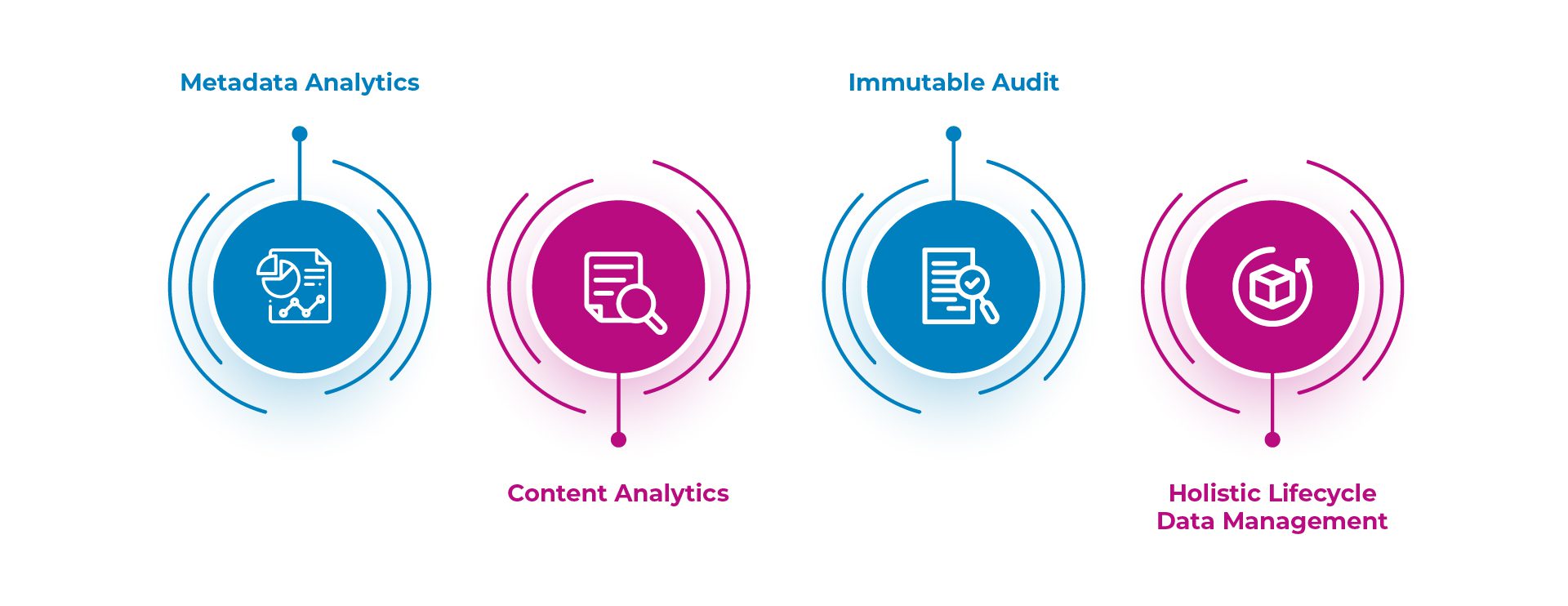
- Metadata Analytics: In the realm of ever increasing data, financial providers possess a potent weapon: metadata analytics. By harnessing the power of specialized software tools like Data Dynamics’ StorageX, these providers can extract and analyze metadata, unraveling valuable insights into the inner workings of their organization’s data. This approach offers a myriad of benefits, illuminating the path towards improved data understanding and utilization.
One of the primary advantages of metadata analytics lies in its ability to unveil patterns in data access and usage. By identifying these patterns, organizations can enhance their data governance and security measures, fortifying their defenses against potential threats. Moreover, metadata analytics serves as a beacon, revealing redundant or outdated data that burdens storage systems. It addresses the challenge of orphaned data, which consumes valuable storage space and poses compliance risks. Armed with this knowledge, organizations can strategically trim their data landscape and reduce their risk exposure, optimizing their resources for greater efficiency. Furthermore, metadata analytics brings about a transformation in the realm of data search and retrieval. By scrutinizing metadata, organizations can develop more precise and efficient search algorithms, empowering users to locate the desired data with ease. This newfound agility enhances management capabilities, allowing for more effective data classification and the application of security controls. As a result, sensitive information gains fortified protection, shielded from unauthorized access and potential breaches.
In the intricate landscape of unstructured data, metadata analytics emerges as a guiding light for financial providers. Its ability to extract and analyze metadata unlocks a treasure trove of insights, unveiling patterns, streamlining storage, and optimizing data search. By embracing metadata analytics, organizations can chart a course towards enhanced data governance, strengthened security, and a more efficient utilization of their invaluable resources. - Content Analytics: In the vast landscape of data analysis, content analytics stands apart from its counterpart, metadata analytics. While metadata analytics focuses on the descriptive aspects of data, content analytics delves into the very essence of meaning and context. This powerful approach unlocks the ability to accurately identify sensitive or private information within unstructured data files, including the likes of personally identifiable information (PII) and business sensitive information.
Content analytics software tools harness the might of advanced logical expressions to generate descriptive and diagnostic analytics. These analytics provide actionable insights into risk exposure, allowing organizations to identify potential vulnerabilities and take proactive measures to mitigate them. This proactive risk mitigation capability becomes a critical weapon in the fight against data breaches and unauthorized access. Moreover, content analytics empowers organizations with scalable data security remediation strategies. For instance, high-risk personal or sensitive files can be automatically relocated to more secure storage, reducing the likelihood of unauthorized exposure. Sensitivity-based quarantining of data and the application of appropriate access controls further fortify data security measures. Additionally, content analytics also aids enterprises in identifying sensitive data in open shares and thereby fixing the permissions for increased security. With these capabilities at their disposal, data custodians can confidently secure their company’s data, ensuring compliance with stringent security regulations while embracing data-driven management strategies.
In the ever-evolving world of data analysis, content analytics emerges as a game-changer. By delving beyond the surface and understanding the true meaning and context of data, organizations gain a powerful ally in their quest for data security. The ability to identify sensitive information, generate actionable insights, and implement scalable security remediation strategies empowers data custodians to safeguard their company’s valuable assets, comply with security regulations, and embrace a future driven by data-driven decision-making. Check out Data Dynamics Insight Analytix for more information. - Immutable Audit: Immutable audit logs are a critical measure for ensuring data integrity and compliance. Its strength lies in its tamper-proof nature, meaning they cannot be altered. These robust records meticulously track every instance of data access, modifications, and user activities, allowing for proactive monitoring and detection of any anomalies or potential breaches and serving as irrefutable evidence of regulatory compliance. By diligently reviewing these logs, financial institutions can identify any red flags, swiftly respond to security incidents, and mitigate potential risks.
Furthermore, immutable audit trails serve as a valuable resource during audits and investigations. The indisputable nature of these records bolsters the credibility of financial institutions, showcasing their adherence to regulatory frameworks and their dedication to maintaining the highest standards of security and compliance. Here’s a software that can help you get started – Data Dynamics ControlX. - Holistic Lifecycle Data Management: In the ever-evolving landscape of finance, where technology plays a pivotal role, holistic data lifecycle management has emerged as an indispensable weapon in the relentless battle against escalating cyber crimes. As financial institutions navigate the treacherous waters of a digital world, they are entrusted with vast amounts of sensitive customer information and proprietary data. To safeguard against the malicious intentions of cyber criminals, a comprehensive approach to data management is imperative. From the moment data is collected, throughout its lifespan, and until its eventual disposal, every stage demands stringent security measures, meticulous monitoring, and proactive response strategies. By adopting holistic data lifecycle management (such as Data Dynamics’ Unified Data Management Platform), finance professionals can fortify their defenses, ensuring data integrity, confidentiality, and availability while empowering themselves to detect, prevent, and swiftly respond to cyber threats. The marriage of advanced technologies, robust encryption protocols, real-time monitoring, and constant vigilance serves as a formidable armor, enabling the finance industry to stay one step ahead in this unrelenting war against cyber criminals.
The Data Dynamics Advantage
It is evident by now that in the fast-paced world of finance, safeguarding data is of paramount importance. This means embracing a holistic approach to data lifecycle management that covers data classification, retention policies, secure disposal, and archiving. By effectively managing the entire data lifecycle, organizations can minimize the risk of unauthorized access, curb data sprawls, and stay compliant with regulatory frameworks.
But here’s the exciting part – our platform is here to revolutionize the way BFSI companies handle their data. With our cutting-edge Unified Data Management Platform, organizations can take control of their data lifecycle and unleash its full potential. Leveraging Content Analytics powered by a state-of-the-art Data Science Engine, our advanced software enables reliable and consistent identification, remediation, quarantine, and audit of PII (Personally Identifiable Information) and business-sensitive data. With AI/ML and NLP capabilities, the software swiftly discovers and classifies data, ensuring efficient filtering of sensitive or private information from unstructured data files with exceptional accuracy. It goes further by employing sophisticated multi-level logical expressions and a combination of logical operators to generate actionable insights into risk exposure, leveraging descriptive and diagnostic analytics.
But that’s not all. Our platform goes the extra mile to secure your sensitive data. It intelligently isolates high-risk sensitive data in secure storage with restricted access, implementing intelligent file access control and file re-permissions. It also helps enterprises identify sensitive data in open shares and fixes the permissions for increased security. With comprehensive functionalities encompassing risk identification, privacy assessment, open share reporting, enhanced storage visibility, and optimized data and infrastructure management, our solution is a one-stop shop for achieving ultimate efficiency and protection.
Stringent adherence to compliance is a must in the finance industry, and our platform has you covered. Through the integration of metadata, context, and content analytics, our Data Dynamics platform delivers a comprehensive solution for intelligent data discovery. This advanced feature enables the identification of fields within the data that are relevant to regulatory requirements, which are then classified using industry-standard compliance and governance templates. Additionally, our data compliance suite offers a robust capability to generate an immutable audit log supported by blockchain technology. This log effectively tracks data access activities, providing a reliable source of information for regulatory compliance and internal data governance reporting purposes. With these powerful features, we ensure a thorough and efficient approach to data compliance and governance within organizations.
With our platform, you can embark on a journey of confident data management, compliance, and governance in the dynamic BFSI sector. Join the ranks of our esteemed clientele, which boasts over 300 enterprises, including 28 Fortune 100 companies and 6 Fortune 100 banks and financial institutions.
Experience the future of data lifecycle management and take your data security to new heights. Visit our website today at www.datadynamicsinc.com to learn more about how our Data Management Platform can empower your organization and drive your success in the digital age. You can also contact us at solutions@datdyn.com I (713)-491-4298.






